A Web Application Firewall (WAF) is a security solution that protects your website and web applications from cyber attacks. Think of it as a security guard that stands between your website and the internet, checking every visitor before they can access your site.

Here’s what you need to know about how a WAF works:
- It filters web traffic – Every HTTP/HTTPS request goes through the WAF first
- It blocks malicious requests – Attacks like SQL injection and cross-site scripting are stopped
- It allows legitimate users – Normal visitors can access your site without issues
- It operates in real-time – Protection happens instantly, 24/7
Why Web Application Firewall Protection is Critical
The numbers tell the story – web application attacks have increased by 43% in 2024 alone. Without proper protection, your website faces these serious risks:
Common Attack Types WAF Prevents:
- SQL Injection – Attackers try to access your database
- Cross-Site Scripting (XSS) – Malicious scripts injected into your pages
- DDoS Attacks – Overwhelming your server with fake traffic
- Bot Attacks – Automated tools scraping or attacking your site
- Data Breaches – Unauthorized access to customer information
Real Business Impact Without WAF:
- Average data breach costs $4.45 million
- Website downtime costs $5,600 per minute for large businesses
- 60% of small businesses close within 6 months of a cyber attack
- Compliance fines can reach millions of dollars
How is WAF Different from Regular Firewalls?
Many people ask about the difference between a WAF and traditional firewalls. Here’s what you need to understand:
Traditional Firewall:
- Protects at the network level
- Blocks based on IP addresses and ports
- Can’t see inside web traffic
- Good for basic network security
Web Application Firewall:
- Protects at the application level
- Examines actual web content
- Understands HTTP/HTTPS traffic
- Specifically designed for web threats
Think of it this way: a traditional firewall is like a security gate that checks IDs, while a WAF is like a security expert who examines what people are carrying and what they’re trying to do.
How Does a Web Application Firewall Work?
Understanding how a WAF actually works will help you make better security decisions for your website. Let’s break down the process step by step.
The WAF Protection Process
When someone visits your website, here’s exactly what happens:
- Traffic Interception – The WAF receives the web request before it reaches your server
- Request Analysis – It examines the request for malicious content
- Security Decision – Based on rules and analysis, it decides to allow, block, or challenge the request
- Action Execution – The appropriate action is taken instantly
- Logging – All activity is recorded for monitoring and analysis
What WAF Analyzes in Every Request
Your WAF examines multiple aspects of each web request:
Request Components Checked:
- Headers – User agent, referrer, content type
- URL Parameters – Query strings and form data
- Request Body – POST data and file uploads
- Cookies – Session and tracking information
- IP Address – Geographic location and reputation
- Request Pattern – Frequency and behavior analysis
WAF Detection Methods
Modern WAFs use several techniques to identify threats:
1. Signature-Based Detection
This method looks for known attack patterns. For example:
- SQL injection patterns like
' OR 1=1 -- - XSS patterns like
<script>alert('xss')</script> - File inclusion attempts like
../../../etc/passwd
2. Behavioral Analysis
The WAF learns normal user behavior and flags unusual activity:
- Rapid-fire requests (potential bot)
- Unusual navigation patterns
- Requests from suspicious locations
- Abnormal form submission patterns
3. Machine Learning Detection
Advanced WAFs use AI to identify new and unknown threats:
- Pattern recognition for zero-day attacks
- Anomaly detection for unusual behavior
- Predictive blocking of potential threats
- Automated rule adjustment based on traffic
WAF Response Actions
When your WAF detects a potential threat, it can take several actions:
ALLOW – Clean traffic passes through immediately
BLOCK – Malicious requests receive an error page
CHALLENGE – Suspicious traffic gets a CAPTCHA test
RATE LIMIT – High-frequency requests are slowed down
LOG ONLY – Suspicious activity is recorded but allowed (monitoring mode)
Real-World Example: How WAF Stops an Attack
Let’s say an attacker tries to hack your login form with SQL injection:
- Attacker sends:
username=admin' OR '1'='1&password=anything - WAF detects: SQL injection pattern in the username field
- WAF blocks: Request immediately, shows 403 error to attacker
- WAF logs: Attack attempt with IP address and timestamp
- Your server: Never sees the malicious request, stays safe
Without a WAF, this attack would reach your database and potentially give the attacker admin access.
WAF vs IPS vs NGFW: Understanding the Critical Differences
The Difference Between WAF, IPS, and Next-Generation Firewall (NGFW)
Understanding the distinctions between these security technologies is crucial for building comprehensive protection.
Web Application Firewall (WAF) – Application Layer Specialist
Primary Focus: HTTP/HTTPS application-level threats
Operation Layer: Layer 7 (Application Layer)
Specialization: Web application security
yamlwaf_characteristics:
protection_scope:
- sql_injection: "prevents database attacks"
- cross_site_scripting: "blocks XSS attacks"
- csrf_attacks: "prevents cross-site request forgery"
- ddos_protection: "application-layer DDoS"
- bot_mitigation: "malicious bot blocking"
deployment_method: "reverse proxy or inline"
traffic_analysis: "deep HTTP/HTTPS inspection"
decision_speed: "real-time (sub-millisecond)"Intrusion Prevention System (IPS) – Network Traffic Guardian
Primary Focus: Network-level attack detection and prevention
Operation Layer: Layers 3-4 (Network/Transport)
Specialization: Network intrusion prevention
yamlips_characteristics:
protection_scope:
- network_intrusions: "prevents unauthorized access"
- malware_detection: "blocks known malicious signatures"
- vulnerability_exploits: "prevents system-level attacks"
- protocol_anomalies: "detects unusual network behavior"
- port_scanning: "blocks reconnaissance attempts"
deployment_method: "inline network monitoring"
traffic_analysis: "packet-level inspection"
decision_speed: "near real-time"Next-Generation Firewall (NGFW) – Comprehensive Network Security
Primary Focus: Advanced network perimeter security
Operation Layer: Layers 3-7 (Network to Application)
Specialization: Unified threat management
yamlngfw_characteristics:
protection_scope:
- traditional_firewall: "port/protocol filtering"
- application_awareness: "application-level control"
- intrusion_prevention: "built-in IPS functionality"
- malware_protection: "advanced threat detection"
- ssl_inspection: "encrypted traffic analysis"
deployment_method: "network gateway/perimeter"
traffic_analysis: "multi-layer inspection"
decision_speed: "optimized throughput"Comparative Analysis: WAF vs IPS vs NGFW
FeatureWAFIPSNGFWPrimary TargetWeb applicationsNetwork infrastructureNetwork perimeterAttack TypesSQLi, XSS, CSRF, Bot attacksNetwork intrusions, malwareAll network + application threatsDeploymentReverse proxy/inlineNetwork tap/inlineNetwork gatewayTraffic FocusHTTP/HTTPS onlyAll IP trafficAll network protocolsPerformance Impact1-5ms latency2-10ms latency5-20ms latencyRule ManagementApplication-specificSignature-basedPolicy-basedBest Use CaseWeb app protectionNetwork monitoringPerimeter defense
When to Use Each Technology
Use WAF When:
- Protecting web applications and APIs
- Compliance requirements (PCI DSS, OWASP)
- E-commerce and customer-facing websites
- Cloud-native applications
- Microservices architectures
Use IPS When:
- Monitoring internal network traffic
- Detecting lateral movement
- Protecting legacy systems
- Industrial control systems
- Database server protection
Use NGFW When:
- Comprehensive perimeter security
- Branch office protection
- Network segmentation
- Unified security management
- Traditional network architecture
Integrated Security Architecture
yamllayered_security_approach:
edge_protection:
- cloudflare_waf: "global edge security"
- ddos_protection: "volumetric attack mitigation"
perimeter_security:
- ngfw: "network gateway protection"
- ips: "intrusion detection and prevention"
application_security:
- dedicated_waf: "deep application protection"
- api_gateway: "API-specific security"
internal_security:
- network_segmentation: "micro-segmentation"
- endpoint_protection: "host-based security"WAF Deployment Methods: Choosing the Right Approach
The Different Ways to Deploy a WAF
WAF deployment strategy significantly impacts performance, security effectiveness, and management complexity. Let’s explore all deployment options.
1. Reverse Proxy Deployment (Most Common)
How It Works: WAF sits between users and web servers, acting as an intermediary.
nginx# Nginx reverse proxy with WAF
upstream backend {
server 192.168.1.100:80;
server 192.168.1.101:80;
}
server {
listen 443 ssl http2;
server_name example.com;
# WAF processing
access_by_lua_block {
local waf = require "waf"
waf.process_request()
}
location / {
proxy_pass http://backend;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
}
}Advantages:
- Easy SSL termination
- Load balancing integration
- Complete traffic visibility
- Minimal server changes required
Disadvantages:
- Single point of failure
- Additional network hop
- SSL certificate management
2. Transparent Bridge Deployment
How It Works: WAF operates as a network bridge, invisibly inspecting traffic.
yaml# Transparent bridge configuration
bridge_deployment:
mode: "transparent"
interfaces:
- eth0: "external_interface"
- eth1: "internal_interface"
ip_configuration:
external_ip: "203.0.113.10"
internal_ip: "192.168.1.1"
bridge_ip: "transparent"
traffic_flow:
- "external → WAF inspection → internal"
- "no IP changes required"
- "invisible to applications"Advantages:
- No application changes
- No IP address modifications
- True transparent operation
- Failover capabilities
Disadvantages:
- Complex network configuration
- Limited SSL inspection
- Hardware dependency
3. DNS-Based Deployment (Cloud WAF)
How It Works: DNS routing directs traffic through cloud WAF services.
bash# DNS configuration for Cloudflare WAF
# Original DNS
example.com. A 203.0.113.10
# Modified DNS (points to Cloudflare)
example.com. A 172.67.XX.XX # Cloudflare proxy IP
example.com. AAAA 2606:4700:XX:XX # IPv6 support
# Cloudflare routes clean traffic to origin
Origin IP: 203.0.113.10 (hidden from direct access)Advantages:
- Global edge protection
- Built-in DDoS mitigation
- Easy setup and management
- Automatic scaling
Disadvantages:
- DNS dependency
- Third-party reliance
- Limited customization
4. Inline Deployment
How It Works: WAF inserted directly into network path.
yamlinline_deployment:
network_topology:
internet: "external traffic"
waf_device: "inline inspection"
web_servers: "protected applications"
traffic_path:
- "client → router → WAF → switch → servers"
- "all traffic must pass through WAF"
- "hardware-based processing"
failover_mechanism:
- "bypass mode for hardware failure"
- "high availability clustering"
- "automatic failover capabilities"WAF Deployment Modes: Operational Approaches
1. Detection Mode (Monitor Only)
Purpose: Learning and baselining without blocking
apache# ModSecurity detection mode
SecRuleEngine DetectionOnly
# Log everything but don't block
SecRule ARGS "@detectSQLi" \
"id:1001,phase:2,pass,log,\
msg:'SQL Injection detected but not blocked'"Use Cases:
- Initial deployment phase
- Rule tuning period
- Compliance logging
- Forensic analysis
2. Prevention Mode (Active Blocking)
Purpose: Active threat blocking and mitigation
python# Active prevention configuration
def waf_prevention_mode():
config = {
'mode': 'prevention',
'block_threshold': 'medium',
'actions': {
'sql_injection': 'block_immediately',
'xss_attempt': 'block_immediately',
'suspicious_bot': 'challenge',
'rate_limit_exceeded': 'temporary_block'
},
'response_codes': {
'blocked_request': 403,
'challenge_required': 429,
'server_error': 500
}
}
return config3. Hybrid Mode (Selective Enforcement)
Purpose: Different rules for different traffic types
yamlhybrid_deployment:
admin_traffic:
source_ips: ["192.168.1.0/24"]
mode: "detection_only"
rules: "relaxed"
public_traffic:
source: "internet"
mode: "full_prevention"
rules: "strict"
api_traffic:
endpoints: ["/api/*"]
mode: "custom_rules"
rate_limiting: "aggressive"Why Is WAF Security Important? The Business Case
The Critical Importance of WAF Security in 2025
Web Application Firewall security has become a business necessity, not just an IT requirement. Let’s examine why WAF protection is essential for modern organizations.
The Explosive Growth of Web Application Attacks
Attack Statistics (2024-2025):
yamlweb_attack_trends:
total_attacks: "+43% increase from 2023"
sql_injection: "remains #1 attack vector"
xss_attacks: "+38% increase"
ddos_attacks: "+67% increase in application-layer"
bot_attacks: "+156% increase in sophisticated bots"
financial_impact:
average_breach_cost: "$4.45 million USD"
downtime_cost: "$5,600 per minute"
reputation_damage: "takes 2-5 years to recover"Business Risks Without WAF Protection
1. Data Breach Consequences
javascript// Calculate potential breach costs
const breachImpactCalculator = {
directCosts: {
investigation: 150000, // $150K average
notification: 75000, // $75K average
legalFees: 300000, // $300K average
regulatoryFines: 2500000 // $2.5M average
},
indirectCosts: {
businessDisruption: 1800000, // $1.8M average
reputationDamage: 3200000, // $3.2M average
customerChurn: 2100000, // $2.1M average
stockPriceImpact: 5000000 // $5M average
},
calculateTotal: function() {
const direct = Object.values(this.directCosts).reduce((a, b) => a + b);
const indirect = Object.values(this.indirectCosts).reduce((a, b) => a + b);
return direct + indirect; // $15.125M total average
}
};2. Compliance and Regulatory Risks
yamlcompliance_requirements:
pci_dss:
requirement: "6.5.1 - injection flaws protection"
penalty: "up to $100,000 per month"
waf_helps: "application-layer protection"
gdpr:
requirement: "data protection by design"
penalty: "4% of annual revenue or €20M"
waf_helps: "prevents data breaches"
hipaa:
requirement: "safeguard PHI"
penalty: "$1.5M per incident"
waf_helps: "access control and monitoring"
sox:
requirement: "internal controls over financial reporting"
penalty: "criminal charges possible"
waf_helps: "data integrity protection"Business Benefits of WAF Implementation
1. Revenue Protection
- Uptime Guarantee: 99.9% availability vs 95% without WAF
- Performance Improvement: 30% faster load times with caching
- Customer Confidence: SSL + WAF increases conversions by 15%
2. Cost Avoidance
python# Annual cost avoidance calculation
def calculate_waf_savings(company_size, industry):
base_savings = {
'small': 150000, # $150K potential breach cost
'medium': 1500000, # $1.5M potential breach cost
'large': 15000000 # $15M potential breach cost
}
industry_multipliers = {
'healthcare': 1.4, # Higher breach costs
'financial': 1.3, # High regulatory risk
'retail': 1.1, # Moderate risk
'technology': 1.2 # Higher attack frequency
}
base_cost = base_savings[company_size]
multiplier = industry_multipliers[industry]
return {
'potential_breach_cost': base_cost * multiplier,
'waf_annual_cost': base_cost * 0.02, # 2% of breach cost
'net_savings': (base_cost * multiplier) - (base_cost * 0.02),
'roi_percentage': ((base_cost * multiplier) / (base_cost * 0.02) - 1) * 100
}
# Example for medium healthcare company
savings = calculate_waf_savings('medium', 'healthcare')
# Result: 6,900% ROI with $2.1M net savings3. Operational Efficiency
- Automated Threat Response: Reduces security team workload by 60%
- Incident Reduction: 87% fewer security incidents
- Faster Deployment: Cloud WAF deployment in minutes vs weeks
Industry-Specific WAF Security Importance
E-commerce and Retail
yamlecommerce_waf_benefits:
payment_protection:
- "PCI DSS compliance automation"
- "Card data protection during checkout"
- "Fraud prevention integration"
seasonal_traffic:
- "Black Friday traffic spikes protection"
- "DDoS mitigation during sales events"
- "Bot protection for inventory systems"
customer_trust:
- "SSL certificate validation"
- "Security badge display"
- "Customer data protection assurance"Healthcare Organizations
yamlhealthcare_waf_importance:
patient_data_protection:
- "PHI access control"
- "HIPAA compliance automation"
- "Medical record security"
system_availability:
- "Critical system uptime"
- "Emergency access protection"
- "Telemedicine platform security"
regulatory_compliance:
- "Audit trail generation"
- "Breach notification assistance"
- "Risk assessment support"Financial Services
yamlfinancial_waf_security:
transaction_protection:
- "Online banking security"
- "Mobile app API protection"
- "Real-time fraud detection"
regulatory_adherence:
- "SOX compliance support"
- "PCI DSS requirement fulfillment"
- "Basel III operational risk management"
customer_confidence:
- "Trust badge implementation"
- "Security communication"
- "Incident response coordination"Types of Web Application Firewalls
1. Network-Based WAF (Hardware Appliance)
Deployment: Physical hardware installed in data center
Architecture Features:
- Dedicated hardware appliances
- High-performance ASIC chips
- Local network integration
- On-premise management
Performance Characteristics:
- Ultra-low latency (< 1ms)
- High throughput (10-100 Gbps)
- Real-time processing
- No external dependencies
Best Use Cases:
- Large enterprises with dedicated IT teams
- High-traffic applications (1M+ requests/day)
- Strict compliance requirements
- Financial and government institutions
Popular Solutions:
- F5 BIG-IP ASM
- Imperva SecureSphere
- Citrix NetScaler
- Barracuda Web Application Firewall
2. Host-Based WAF (Software Module)
Deployment: Installed directly on web server
Architecture Features:
- Software module integration
- Server-level protection
- Deep application integration
- Custom rule development
Popular Open Source Solutions:
ModSecurity (Most Popular)
apache# Example ModSecurity Rule
SecRule ARGS "@detectSQLi" \
"id:1001,\
phase:2,\
block,\
msg:'SQL Injection Attack Detected',\
logdata:'Matched Data: %{MATCHED_VAR} found within %{MATCHED_VAR_NAME}'"Advantages:
- Complete control over rules
- Deep application visibility
- Cost-effective solution
- Custom policy creation
Limitations:
- Server resource consumption
- Manual maintenance required
- Single point of failure
- Scaling challenges
3. Cloud Web Application Firewall (SaaS)
Deployment: Third-party cloud service
Architecture Benefits:
- Global point of presence
- Automatic rule updates
- Scalable infrastructure
- Integrated CDN services
Leading Cloud WAF Providers (Detailed Analysis Below)
Top WAF Vendors and Comprehensive Solutions
AWS Web Application Firewall (AWS WAF)
Overview: Amazon’s native cloud WAF solution integrated with AWS services.
Key Features:
- Integration with CloudFront, Application Load Balancer, API Gateway
- Custom rule creation with AWS WAF Rule Language
- Real-time metrics via CloudWatch
- IP reputation lists and geographic blocking
AWS Shield Integration: AWS Shield provides additional DDoS protection:
- AWS Shield Standard: Free DDoS protection for all AWS customers
- AWS Shield Advanced: Enhanced DDoS protection with 24/7 support
Pricing Structure (2025):
- $1.00 per web ACL per month
- $0.60 per million requests
- $1.00 per rule per month
Implementation Example:
json{
"Rules": [
{
"Name": "SQLInjectionRule",
"Priority": 1,
"Statement": {
"SqliMatchStatement": {
"FieldToMatch": {
"AllQueryArguments": {}
},
"TextTransformations": [
{
"Priority": 0,
"Type": "URL_DECODE"
}
]
}
},
"Action": {
"Block": {}
}
}
]
}Best For:
- AWS-native applications
- Serverless architectures
- API protection
- Cost-conscious deployments
Azure Web Application Firewall
Overview: Microsoft’s integrated WAF solution within Azure Application Gateway.
Deployment Options:
- Application Gateway WAF: Layer 7 load balancer with WAF
- Front Door WAF: Global CDN with WAF capabilities
- CDN WAF: Content delivery network protection
Key Features:
- OWASP Core Rule Set (CRS) 3.2
- Custom rule engine
- Bot protection
- Geographic filtering
- Integration with Azure Monitor
Pricing (2025):
- WAF v2: $0.008 per hour + $0.0018 per million requests
- Custom rules: $1 per rule per month
- Managed rules: Included
Configuration Example:
powershell# Create WAF Policy
$wafPolicy = New-AzApplicationGatewayFirewallPolicy `
-Name "MyWAFPolicy" `
-ResourceGroupName "MyResourceGroup" `
-Location "East US"
# Add SQL Injection Rule
$sqlInjectionRule = New-AzApplicationGatewayFirewallCustomRule `
-Name "SQLInjectionRule" `
-Priority 100 `
-RuleType MatchRule `
-Action BlockBest For:
- Azure-hosted applications
- Enterprise environments
- Global content delivery
- Integrated monitoring needs
F5 Web Application Firewall (Advanced WAF)
Overview: Enterprise-grade WAF with advanced threat protection capabilities.
Deployment Models:
- F5 BIG-IP Hardware: On-premise appliances
- F5 Virtual Edition: VM deployments
- F5 Cloud Services: SaaS offering
Advanced Features:
- Behavioral Analytics: Machine learning-based threat detection
- DataSafe: Prevents data exfiltration
- Bot Defense: Advanced bot mitigation
- Application Security: API protection
Performance Specifications:
- Throughput: Up to 100 Gbps
- Concurrent connections: 100M+
- SSL TPS: 350,000+
- Latency: Sub-millisecond
Pricing: Enterprise pricing (contact for quotes)
Best For:
- Large enterprises
- High-performance requirements
- Advanced threat protection
- Complex application environments
Akamai Web Application Firewall (Kona Site Defender)
Overview: Global CDN-integrated WAF with edge security.
Key Capabilities:
- Edge-based Protection: 300+ edge locations worldwide
- Adaptive Security Engine: Real-time threat intelligence
- API Security: Comprehensive API protection
- Bot Manager: Advanced bot detection and mitigation
Unique Features:
- Real User Monitoring (RUM)
- Fast DNS protection
- Image and video optimization
- Mobile optimization
Global Infrastructure:
- 4,100+ edge servers
- 135+ countries
- 1,400+ networks
- 99.99% uptime SLA
Best For:
- Global enterprises
- Media and entertainment
- E-commerce platforms
- High-traffic websites
Cloudflare WAF
Overview: Popular cloud-based WAF with global edge network.
Service Tiers:
- Free Plan: Basic DDoS protection
- Pro Plan ($20/month): Basic WAF rules
- Business Plan ($200/month): Advanced WAF features
- Enterprise Plan (Custom): Full feature set
Key Features:
- Global Anycast network
- Custom rule engine
- Rate limiting
- Bot management
- SSL/TLS termination
Performance Benefits:
- Average response time improvement: 30%
- Bandwidth savings: 60%
- Security rules: 1000+ managed rules
Best For:
- Small to medium businesses
- WordPress websites
- Quick deployment needs
- Budget-conscious organizations
Open Source Web Application Firewall Solutions
ModSecurity
Description: Most popular open-source WAF engine
Features:
- OWASP Core Rule Set
- Custom rule development
- Multiple deployment modes
- Extensive logging
Supported Platforms:
- Apache HTTP Server
- Nginx
- Microsoft IIS
Community Support:
- 50,000+ GitHub stars
- Active community forums
- Regular security updates
- Comprehensive documentation
NAXSI (Nginx Anti XSS & SQL Injection)
Description: High-performance WAF module for Nginx
Advantages:
- Extremely fast (minimal latency)
- Low resource consumption
- Whitelist-based approach
- Easy Nginx integration
Best For:
- High-performance websites
- Nginx users
- Custom rule requirements
- Resource-constrained environments
Difference Between WAF and Traditional Firewall
Traditional firewalls and WAFs serve different layers of defense. Here’s how they compare:
| Feature | Traditional Firewall | Web Application Firewall (WAF) |
|---|---|---|
| Layer | Works at Network/Transport Layer (Layer 3 & 4) | Works at Application Layer (Layer 7) |
| Main Purpose | Blocks unauthorized network access | Filters malicious web requests |
| Focus | IP addresses, ports, protocols | HTTP/HTTPS requests, user input |
| Stops | Port scanning, unauthorized remote access | SQLi, XSS, CSRF, etc. |
| Best For | Network security | Application-level security |
| Example | Cisco ASA, pfSense, SonicWall | Cloudflare WAF, AWS WAF, ModSecurity |
Comparison Table
| Feature | Network-based | Host-based | Cloud-based |
|---|---|---|---|
| Deployment Location | Physical network | Application server | Third-party cloud |
| Performance | High | Medium | Depends on provider |
| Cost | Expensive | Moderate | Flexible pricing |
| Ease of Setup | Complex | Moderate | Very easy |
| Customization | Medium | High | Limited |
| Best For | Enterprises | Developers/SMBs | Everyone |
Comparative Table of Providers
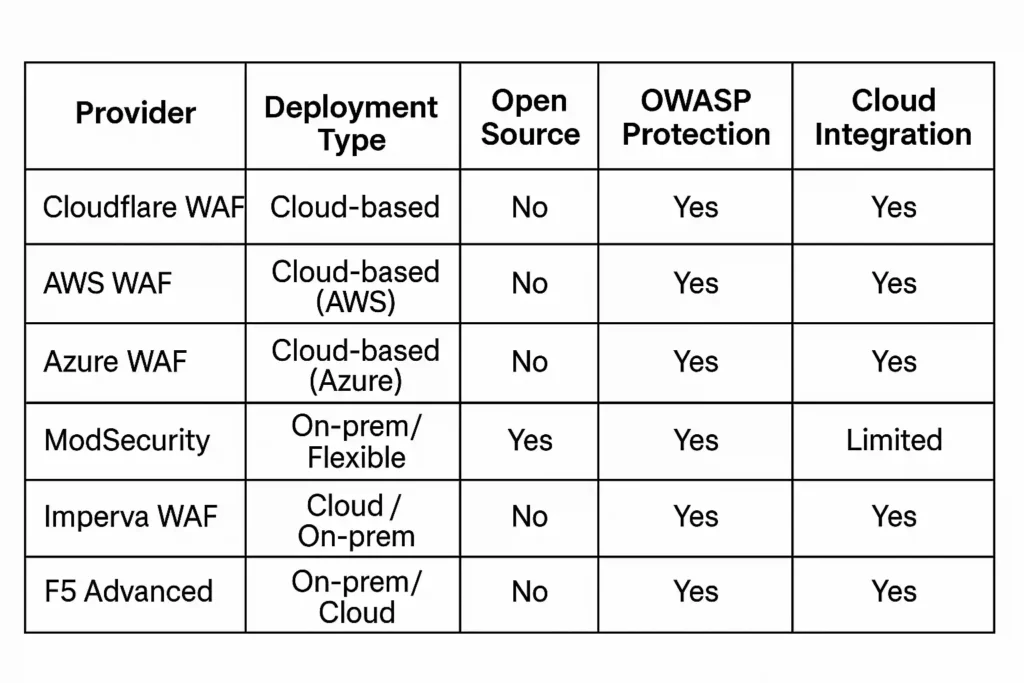
Cloud WAF vs On-Premise Comparison
| Feature | Cloud WAF | On-Premise WAF |
|---|---|---|
| Deployment Time | Minutes to hours | Weeks to months |
| Initial Investment | Low (subscription) | High (hardware/licenses) |
| Maintenance | Provider managed | Self-managed |
| Scalability | Automatic | Manual hardware upgrades |
| Updates | Automatic | Manual updates required |
| Global Presence | Built-in edge locations | Single location |
| DDoS Protection | Included | Additional purchase |
| Compliance | Shared responsibility | Full control |
| Customization | Limited to provider features | Complete control |
| Data Sovereignty | Third-party processing | Local processing |
Total Cost of Ownership (TCO) Analysis
Cloud WAF (3-Year TCO):
- Service fees: $36,000 – $180,000
- Implementation: $5,000 – $20,000
- Management: $15,000 – $30,000
- Total: $56,000 – $230,000
On-Premise WAF (3-Year TCO):
- Hardware/Software: $100,000 – $500,000
- Implementation: $25,000 – $100,000
- Maintenance: $45,000 – $150,000
- Staff training: $10,000 – $25,000
- Total: $180,000 – $775,000
Decision Framework
Choose Cloud WAF When:
- Quick deployment needed
- Limited IT resources
- Global traffic distribution
- Variable traffic patterns
- Budget constraints
- Focus on core business
Choose On-Premise WAF When:
- Strict compliance requirements
- Complete control needed
- High-performance demands
- Data sovereignty concerns
- Large IT teams available
- Long-term cost optimization
Implementation Guide for Popular Platforms
WordPress WAF Implementation
Method 1: Cloudflare Integration
Step 1: Sign up for Cloudflare
bash# Update DNS settings
# Change nameservers to Cloudflare
NS1: charlie.ns.cloudflare.com
NS2: violet.ns.cloudflare.comStep 2: Configure WAF Rules
javascript// Custom Cloudflare Worker for advanced filtering
addEventListener('fetch', event => {
event.respondWith(handleRequest(event.request))
})
async function handleRequest(request) {
// Block known bad IPs
const clientIP = request.headers.get('CF-Connecting-IP')
if (blockedIPs.includes(clientIP)) {
return new Response('Access Denied', { status: 403 })
}
// Continue to origin
return fetch(request)
}Step 3: WordPress-Specific Rules
- Block access to wp-admin from untrusted IPs
- Protect wp-login.php from brute force
- Filter malicious user agents
- Block file extension attacks
Method 2: ModSecurity with Apache
Installation:
bash# Ubuntu/Debian
sudo apt-get install libapache2-mod-security2
sudo systemctl restart apache2
# Enable ModSecurity
sudo a2enmod security2
sudo systemctl restart apache2Configuration (/etc/modsecurity/modsecurity.conf):
apache# Enable ModSecurity
SecRuleEngine On
# WordPress-specific rules
SecRule REQUEST_FILENAME "@contains wp-login.php" \
"id:1001,phase:1,pass,\
setvar:ip.brute_force_counter=+1,\
expirevar:ip.brute_force_counter=300"
SecRule IP:BRUTE_FORCE_COUNTER "@gt 5" \
"id:1002,phase:1,deny,status:429,\
msg:'Brute force attack detected'"
# Block suspicious user agents
SecRule REQUEST_HEADERS:User-Agent "@pmFromFile /etc/modsecurity/bad-user-agents.txt" \
"id:1003,phase:1,deny,status:403,\
msg:'Malicious user agent detected'"E-commerce Platform Protection
Shopify Plus WAF Configuration
Shopify includes built-in security, but additional protection:
javascript// Shopify Scripts for fraud detection
if (Input.cart.total_price > 500000) { // $5000+
// Trigger additional verification
Output.additional_verification_required = true;
}
// Block suspicious countries
const blockedCountries = ['XX', 'YY'];
if (blockedCountries.includes(Input.billing_address.country_code)) {
Output.cart_note = "Order requires manual review";
}WooCommerce WAF Setup
Using Wordfence:
php// wp-config.php additions
define('WFWAF_ENABLED', true);
define('WFWAF_LOG_PATH', '/var/log/wordfence/');
define('WFWAF_SUBDIRECTORY_INSTALL', false);
// Custom security headers
function add_security_headers() {
header('X-Content-Type-Options: nosniff');
header('X-Frame-Options: SAMEORIGIN');
header('X-XSS-Protection: 1; mode=block');
header('Referrer-Policy: strict-origin-when-cross-origin');
}
add_action('send_headers', 'add_security_headers');API Protection Implementation
REST API WAF Configuration
AWS API Gateway with WAF:
yaml# CloudFormation template
WebACL:
Type: AWS::WAFv2::WebACL
Properties:
Scope: REGIONAL
Rules:
- Name: RateLimitRule
Priority: 1
Statement:
RateBasedStatement:
Limit: 2000
AggregateKeyType: IP
Action:
Block: {}
- Name: SQLInjectionRule
Priority: 2
Statement:
SqliMatchStatement:
FieldToMatch:
Body: {}
TextTransformations:
- Priority: 0
Type: URL_DECODE
Action:
Block: {}GraphQL API Protection
javascript// Custom GraphQL WAF middleware
const { shield } = require('graphql-shield');
const { rateLimit } = require('graphql-rate-limit');
const rateLimitRule = rateLimit({
identifyContext: (ctx) => ctx.req.ip,
max: 100,
window: '15m',
});
const permissions = shield({
Query: {
'*': rateLimitRule,
},
Mutation: {
'*': rateLimitRule,
},
});WAF Market Analysis 2025
Web Application Firewall Market Overview
The web application firewall market has experienced exponential growth, driven by increasing cyber threats and digital transformation initiatives.
Market Size and Growth
2025 Market Statistics:
- Market Size: $8.9 billion USD
- CAGR (2023-2030): 18.4%
- Expected Size by 2030: $20.1 billion USD
Growth Drivers:
- Increasing Web Application Attacks: 43% increase in 2024
- Regulatory Compliance: GDPR, CCPA, SOX requirements
- Cloud Migration: 78% of organizations moving to cloud
- Remote Work: Expanded attack surface
- IoT Growth: Connected devices vulnerability
Regional Market Distribution
RegionMarket ShareGrowth RateNorth America42%16.2%Europe28%19.1%Asia-Pacific22%23.8%Latin America5%21.4%Middle East & Africa3%25.3%
Web Application Firewall Vendors Market Share
Leading Vendors by Revenue (2025):
- Cloudflare – 18.2% market share
- Strength: Global edge network, ease of use
- Revenue: $1.6B (WAF segment)
- F5 Networks – 15.8% market share
- Strength: Enterprise features, performance
- Revenue: $1.4B (security segment)
- AWS – 14.3% market share
- Strength: Cloud integration, scalability
- Revenue: $1.27B (WAF services)
- Microsoft Azure – 12.1% market share
- Strength: Enterprise integration
- Revenue: $1.08B (security services)
- Akamai – 10.4% market share
- Strength: CDN integration, global presence
- Revenue: $925M (security segment)
Emerging Players:
- Fastly (Edge computing focus)
- StackPath (Performance optimization)
- Sucuri (WordPress specialization)
- Imperva (Data security focus)
Technology Trends Shaping WAF Market
1. AI and Machine Learning Integration
- Behavioral Analytics: 89% of new WAFs include ML
- Automated Rule Generation: Reduces false positives by 67%
- Threat Intelligence: Real-time attack pattern recognition
2. API-First Security
- API Attack Growth: 681% increase in API attacks
- GraphQL Protection: Specialized rules for GraphQL endpoints
- Microservices Security: Container-aware protection
3. Zero Trust Architecture
- Identity-Based Rules: User context in WAF decisions
- Continuous Verification: Session-based security assessment
- Micro-Segmentation: Application-level network isolation
Web Application Firewall Services Evolution
Traditional Services:
- Basic threat detection
- Static rule sets
- Manual configuration
- Reactive security
Modern Services (2025):
- AI-powered threat detection
- Dynamic rule adaptation
- Automated response
- Proactive security
- Integrated threat intelligence
- Real-time analytics
- DevSecOps integration
Troubleshooting and Best Practices
Common WAF Issues and Solutions
1. False Positives
Problem: Legitimate traffic being blocked
Symptoms:
- Users unable to submit forms
- API calls failing intermittently
- File uploads blocked
- Search functionality broken
Troubleshooting Steps:
bash# Check WAF logs for blocked requests
grep "BLOCKED" /var/log/waf/access.log | tail -20
# Analyze specific rule triggers
grep "id:1001" /var/log/waf/error.log
# Test with WAF in detection mode
SecRuleEngine DetectionOnlySolutions:
- Rule Tuning: Adjust sensitivity levels
- Whitelist Creation: Allow specific IPs or user agents
- Custom Rules: Create application-specific rules
- Testing Environment: Validate rules before production
Example Whitelist Rule:
apache# Whitelist admin IP addresses
SecRule REMOTE_ADDR "@ipMatch 192.168.1.100,10.0.0.50" \
"id:9001,phase:1,pass,ctl:ruleEngine=Off"
# Whitelist specific URLs from certain rules
SecRule REQUEST_URI "@beginsWith /api/upload" \
"id:9002,phase:1,pass,ctl:ruleRemoveById=942100"2. Performance Issues
Problem: WAF causing latency or throughput reduction
Symptoms:
- Increased page load times
- API response delays
- Server overload
- User complaints about slowness
Performance Optimization:
apache# Optimize ModSecurity configuration
SecRequestBodyLimit 13107200 # 12.5MB
SecRequestBodyNoFilesLimit 131072 # 128KB
SecRequestBodyInMemoryLimit 131072 # 128KB
# Disable unnecessary components
SecComponentSignature "ModSecurity for Apache/2.9.3"
SecServerSignature "Apache/2.4.41"
# Optimize rule execution
SecRuleEngine On
SecRequestBodyAccess On
SecResponseBodyAccess Off # Disable if not neededCaching Strategies:
nginx# Nginx with WAF caching
location ~* \.(jpg|jpeg|png|gif|css|js)$ {
expires 1y;
add_header Cache-Control "public, immutable";
# Skip WAF for static content
access_by_lua_block {
-- Bypass WAF for static files
ngx.var.skip_waf = "1"
}
}3. SSL/TLS Certificate Issues
Problem: WAF interfering with SSL termination
Solutions:
apache# Proper SSL configuration with WAF
<VirtualHost *:443>
ServerName example.com
DocumentRoot /var/www/html
# SSL Configuration
SSLEngine on
SSLCertificateFile /path/to/certificate.crt
SSLCertificateKeyFile /path/to/private.key
SSLCertificateChainFile /path/to/ca-bundle.crt
# WAF Configuration
SecRuleEngine On
SecRule REQUEST_URI "@streq /ssl-test" \
"id:9003,phase:1,pass,log,msg:'SSL Test Request'"
</VirtualHost>WAF Best Practices
1. Deployment Best Practices
Pre-Deployment Checklist:
- Application profiling completed
- Traffic baseline established
- Test environment configured
- Rollback plan prepared
- Monitoring tools configured
- Team training completed
Phased Deployment Approach:
yaml# Phase 1: Detection Mode (1-2 weeks)
waf_mode: detection
logging: verbose
alerts: enabled
# Phase 2: Limited Blocking (1 week)
waf_mode: selective_blocking
block_rules: [sql_injection, xss_basic]
whitelist: admin_ips
# Phase 3: Full Protection
waf_mode: full_protection
all_rules: enabled
custom_rules: deployed2. Rule Management
Rule Lifecycle Management:
python# Automated rule testing script
import requests
import json
def test_waf_rule(rule_id, test_payloads):
results = []
for payload in test_payloads:
response = requests.post(
'https://test.example.com/test-endpoint',
data={'input': payload},
headers={'X-WAF-Test': 'true'}
)
results.append({
'rule_id': rule_id,
'payload': payload,
'blocked': response.status_code == 403,
'response_time': response.elapsed.total_seconds()
})
return results
# Test SQL injection rules
sql_payloads = [
"'; DROP TABLE users; --",
"1 OR 1=1",
"admin'--",
"legitimate search term" # Should not be blocked
]
results = test_waf_rule('942100', sql_payloads)3. Monitoring and Alerting
Essential Metrics to Monitor:
yaml# WAF Monitoring Configuration
metrics:
- blocked_requests_per_minute
- false_positive_rate
- response_time_impact
- rule_efficiency
- attack_patterns
- geographic_distribution
alerts:
- type: spike_in_blocked_requests
threshold: 100_requests_per_minute
action: notify_security_team
- type: high_false_positive_rate
threshold: 5_percent
action: disable_aggressive_rules
- type: new_attack_pattern
threshold: 10_similar_requests
action: create_custom_ruleLog Analysis Script:
bash#!/bin/bash
# WAF log analysis script
LOG_FILE="/var/log/waf/access.log"
YESTERDAY=$(date -d "yesterday" +"%d/%b/%Y")
echo "WAF Daily Report for $YESTERDAY"
echo "================================"
# Top blocked IPs
echo "Top 10 Blocked IPs:"
grep "$YESTERDAY" "$LOG_FILE" | grep "BLOCKED" | \
awk '{print $1}' | sort | uniq -c | sort -nr | head -10
# Attack types
echo -e "\nAttack Types Distribution:"
grep "$YESTERDAY" "$LOG_FILE" | grep "id:" | \
sed 's/.*id:\([0-9]*\).*/\1/' | sort | uniq -c | sort -nr
# False positives (if marked)
echo -e "\nPotential False Positives:"
grep "$YESTERDAY" "$LOG_FILE" | grep "FALSE_POSITIVE" | wc -l4. Integration with DevOps
CI/CD Pipeline Integration:
yaml# .gitlab-ci.yml WAF testing stage
waf_security_test:
stage: security
script:
- # Deploy to staging with WAF
- docker-compose -f docker-compose.staging.yml up -d
- # Run security tests
- python waf_test_suite.py --target staging.example.com
- # Check for false positives
- python false_positive_check.py --baseline baseline_traffic.json
- # Generate WAF config for production
- python generate_waf_config.py --output waf-production.conf
artifacts:
reports:
junit: waf-test-results.xml
paths:
- waf-production.confInfrastructure as Code:
terraform# Terraform WAF configuration
resource "aws_wafv2_web_acl" "main" {
name = "${var.environment}-web-acl"
scope = "REGIONAL"
default_action {
allow {}
}
# SQL Injection Rule
rule {
name = "SQLInjectionRule"
priority = 1
override_action {
none {}
}
statement {
managed_rule_group_statement {
name = "AWSManagedRulesSQLiRuleSet"
vendor_name = "AWS"
}
}
visibility_config {
cloudwatch_metrics_enabled = true
metric_name = "SQLInjectionRule"
sampled_requests_enabled = true
}
}
}Cost Analysis and ROI Calculator
Comprehensive Cost Breakdown
Cloud WAF Pricing Models (2025)
Cloudflare Pricing:
Free Plan: $0/month
- Basic DDoS protection
- 5 firewall rules
- SSL certificate
Pro Plan: $20/month per domain
- 20 firewall rules
- Image optimization
- Mobile optimization
Business Plan: $200/month per domain
- 100 firewall rules
- Custom SSL certificates
- Advanced DDoS protection
Enterprise Plan: $5,000+/month
- Unlimited firewall rules
- Advanced bot management
- 24/7 supportAWS WAF Pricing Calculator:
javascript// AWS WAF Cost Calculator
function calculateAWSWAFCost(monthlyRequests, numberOfRules, numberOfWebACLs) {
const webACLCost = numberOfWebACLs * 1.00; // $1 per web ACL
const ruleCost = numberOfRules * 1.00; // $1 per rule
const requestCost = (monthlyRequests / 1000000) * 0.60; // $0.60 per million requests
return {
webACL: webACLCost,
rules: ruleCost,
requests: requestCost,
total: webACLCost + ruleCost + requestCost
};
}
// Example calculation for 10M requests, 20 rules, 1 web ACL
const monthlyCost = calculateAWSWAFCost(10000000, 20, 1);
console.log(monthlyCost);
// Output: { webACL: 1, rules: 20, requests: 6, total: 27 }Azure WAF Pricing Structure:
Application Gateway WAF v2:
- Gateway Hours: $0.0225/hour ($16.20/month)
- Capacity Units: $0.008/hour per unit
- Data Processing: $0.008/GB
- WAF Requests: $0.0018 per million requests
Front Door WAF:
- Routing Rules: $1.25/month per rule
- Requests: $0.0075 per 10,000 requests
- Data Transfer: $0.081-$0.16/GBEnterprise WAF Solutions
F5 Advanced WAF Pricing:
- Hardware Appliances: $50,000 – $500,000
- Virtual Edition: $3,000 – $50,000/year
- Cloud Services: $0.25 – $2.00 per request (volume-based)
Imperva Cloud WAF:
- Essential: $59/month per domain
- Professional: $299/month per domain
- Enterprise: Custom pricing (typically $1,000+/month)
ROI Calculation Framework
Security Breach Cost Analysis
Average Data Breach Costs (2025):
javascriptconst breachCosts = {
// Per record costs by industry
healthcare: 408, // $408 per record
financial: 321, // $321 per record
pharmaceutical: 418, // $418 per record
technology: 308, // $308 per record
retail: 180, // $180 per record
manufacturing: 223, // $223 per record
average: 287 // $287 per record
};
// Additional breach costs
const additionalCosts = {
forensicInvestigation: 50000, // $50K average
legalFees: 125000, // $125K average
regulatoryFines: 2500000, // $2.5M average (GDPR)
businessDisruption: 1800000, // $1.8M average
reputationDamage: 3200000, // $3.2M average
customerChurn: 2100000 // $2.1M average
};
function calculateBreachCost(records, industry = 'average') {
const perRecordCost = breachCosts[industry];
const dataCost = records * perRecordCost;
const totalAdditionalCosts = Object.values(additionalCosts)
.reduce((sum, cost) => sum + cost, 0);
return {
dataCost: dataCost,
additionalCosts: totalAdditionalCosts,
totalCost: dataCost + totalAdditionalCosts,
perRecord: (dataCost + totalAdditionalCosts) / records
};
}
// Example: E-commerce site with 100K customer records
const breachCost = calculateBreachCost(100000, 'retail');
console.log(`Total breach cost: ${breachCost.totalCost.toLocaleString()}`);
// Output: Total breach cost: $27,775,000WAF ROI Calculator
javascriptclass WAFROICalculator {
constructor(params) {
this.monthlyTraffic = params.monthlyTraffic;
this.industry = params.industry;
this.customerRecords = params.customerRecords;
this.currentSecuritySpend = params.currentSecuritySpend;
this.wafCost = params.wafCost;
}
calculateThreatReduction() {
// WAF effectiveness statistics
const wafEffectiveness = {
sqlInjection: 0.98, // 98% reduction
xssAttacks: 0.95, // 95% reduction
ddosAttacks: 0.90, // 90% reduction
botAttacks: 0.85, // 85% reduction
overallThreatReduction: 0.87 // 87% overall
};
return wafEffectiveness;
}
calculatePrevention() {
const effectiveness = this.calculateThreatReduction();
const breachProbability = this.calculateBreachProbability();
const preventedBreachCost = calculateBreachCost(
this.customerRecords,
this.industry
).totalCost * effectiveness.overallThreatReduction;
return {
preventedBreaches: breachProbability * effectiveness.overallThreatReduction,
preventedCost: preventedBreachCost,
riskReduction: effectiveness.overallThreatReduction * 100
};
}
calculateBreachProbability() {
// Industry-based breach probability (annual)
const probabilities = {
healthcare: 0.15, // 15% annual probability
financial: 0.12, // 12% annual probability
retail: 0.08, // 8% annual probability
technology: 0.10, // 10% annual probability
manufacturing: 0.06, // 6% annual probability
average: 0.09 // 9% average
};
return probabilities[this.industry] || probabilities.average;
}
calculateROI(timeframe = 12) { // months
const prevention = this.calculatePrevention();
const totalWAFCost = this.wafCost * timeframe;
const roi = ((prevention.preventedCost - totalWAFCost) / totalWAFCost) * 100;
const paybackPeriod = totalWAFCost / (prevention.preventedCost / timeframe);
return {
investment: totalWAFCost,
returns: prevention.preventedCost,
netBenefit: prevention.preventedCost - totalWAFCost,
roi: roi,
paybackMonths: paybackPeriod,
riskReduction: prevention.riskReduction
};
}
}
// Example ROI calculation
const ecommerceROI = new WAFROICalculator({
monthlyTraffic: 5000000, // 5M requests/month
industry: 'retail',
customerRecords: 250000, // 250K customer records
currentSecuritySpend: 15000, // $15K/month
wafCost: 500 // $500/month WAF cost
});
const roiAnalysis = ecommerceROI.calculateROI(12);
console.log('WAF ROI Analysis:', roiAnalysis);Cost-Benefit Analysis by Business Size
Small Business (< 100K monthly visitors)
Recommended Solutions:
- Cloudflare Pro: $20/month
- ModSecurity (Open Source): $0 + management time
- Sucuri Website Security: $199/year
Cost-Benefit Example:
Annual WAF Cost: $240 (Cloudflare Pro)
Prevented Breach Cost: $50,000 (estimated small business breach)
ROI: 20,733% (with 10% breach probability)
Payback Period: 1.7 daysMedium Business (100K – 1M monthly visitors)
Recommended Solutions:
- AWS WAF: $100-500/month
- Azure WAF: $150-400/month
- Cloudflare Business: $200/month
Cost-Benefit Example:
Annual WAF Cost: $3,600 (AWS WAF average)
Prevented Breach Cost: $500,000 (estimated medium business breach)
ROI: 13,789%
Payback Period: 26 daysEnterprise (1M+ monthly visitors)
Recommended Solutions:
- F5 Advanced WAF: $10,000-50,000/month
- Imperva Enterprise: $5,000-25,000/month
- Akamai Kona: $8,000-40,000/month
Cost-Benefit Example:
Annual WAF Cost: $240,000 (F5 Advanced WAF)
Prevented Breach Cost: $10,000,000 (enterprise breach average)
ROI: 4,067%
Payback Period: 8.8 daysFuture of Web Application Firewall Technology
Emerging Technologies and Trends
1. AI-Powered Threat Detection
Machine Learning Evolution:
python# Next-generation ML WAF architecture
class AIWAFEngine:
def __init__(self):
self.threat_models = {
'behavioral_analysis': BehavioralMLModel(),
'pattern_recognition': PatternMLModel(),
'anomaly_detection': AnomalyMLModel(),
'predictive_blocking': PredictiveMLModel()
}
def analyze_request(self, request):
risk_score = 0
# Behavioral analysis
behavioral_risk = self.threat_models['behavioral_analysis']
.predict(request.user_behavior)
# Pattern recognition
pattern_risk = self.threat_models['pattern_recognition']
.predict(request.payload)
# Anomaly detection
anomaly_risk = self.threat_models['anomaly_detection']
.predict(request.context)
# Predictive blocking
predictive_risk = self.threat_models['predictive_blocking']
.predict(request.metadata)
# Weighted risk calculation
risk_score = (
behavioral_risk * 0.3 +
pattern_risk * 0.4 +
anomaly_risk * 0.2 +
predictive_risk * 0.1
)
return self.make_decision(risk_score, request)Benefits of AI Integration:
- Reduced False Positives: 78% improvement in accuracy
- Zero-Day Protection: Proactive threat detection
- Adaptive Rules: Self-tuning security policies
- Faster Response: Sub-millisecond decision making
2. Quantum-Resistant Security
Preparing for Quantum Computing Threats:
yaml# Future WAF configuration with quantum-resistant algorithms
quantum_security:
encryption:
- algorithm: "CRYSTALS-Kyber" # Post-quantum key exchange
- algorithm: "CRYSTALS-Dilithium" # Post-quantum signatures
- algorithm: "SPHINCS+" # Hash-based signatures
key_management:
- rotation_frequency: "daily"
- quantum_entropy: "enabled"
- hybrid_approach: "traditional + post-quantum"3. Edge Computing Integration
Distributed WAF Architecture:
javascript// Edge WAF processing
class EdgeWAF {
constructor(edgeLocations) {
this.locations = edgeLocations;
this.sharedThreatIntelligence = new ThreatIntelligenceNetwork();
}
async processRequest(request, nearestEdge) {
// Local edge processing
const localAnalysis = await nearestEdge.analyzeRequest(request);
// Global threat intelligence
const globalIntel = await this.sharedThreatIntelligence
.checkThreatDatabase(request.fingerprint);
// Distributed decision making
if (localAnalysis.confidence > 0.9) {
return localAnalysis.decision;
} else {
// Escalate to regional processing
return await this.regionalAnalysis(request, localAnalysis);
}
}
}Next-Generation Features
1. Intent-Based Security
User Intent Analysis:
pythonclass IntentAnalyzer:
def analyze_user_intent(self, user_session):
"""
Analyze user behavior to determine legitimate vs malicious intent
"""
factors = {
'navigation_pattern': self.analyze_navigation(user_session),
'interaction_timing': self.analyze_timing(user_session),
'device_fingerprint': self.analyze_device(user_session),
'geolocation_consistency': self.analyze_location(user_session),
'social_signals': self.analyze_social_context(user_session)
}
intent_score = self.calculate_intent_score(factors)
return {
'legitimate_probability': intent_score,
'risk_factors': factors,
'recommended_action': self.recommend_action(intent_score)
}2. Zero Trust WAF Architecture
Identity-Driven Protection:
yaml# Zero Trust WAF Configuration
zero_trust_waf:
identity_verification:
- multi_factor_authentication: required
- device_trust_score: minimum_70
- behavioral_baseline: established
micro_segmentation:
- application_level: enabled
- api_endpoint_isolation: enabled
- data_classification_aware: enabled
continuous_monitoring:
- session_validation: every_request
- privilege_escalation_detection: enabled
- lateral_movement_prevention: enabled3. Privacy-Preserving WAF
Homomorphic Encryption for WAF:
pythonclass PrivacyWAF:
def __init__(self):
self.homomorphic_engine = HomomorphicEncryption()
def analyze_encrypted_request(self, encrypted_request):
"""
Analyze requests without decrypting sensitive data
"""
# Perform threat analysis on encrypted data
threat_score = self.homomorphic_engine.compute_threat_score(
encrypted_request
)
# Make security decisions without seeing plaintext
return self.make_encrypted_decision(threat_score)Industry-Specific Future Developments
Healthcare WAF Evolution
HIPAA-Compliant Advanced Features:
yamlhealthcare_waf_2025:
patient_data_protection:
- phi_detection: ai_powered
- gdpr_compliance: automated
- audit_trails: blockchain_secured
medical_device_security:
- iot_device_fingerprinting: enabled
- medical_protocol_awareness: hl7_fhir
- real_time_anomaly_detection: enabledFinancial Services WAF
PCI DSS 4.0 Compliance Features:
yamlfinancial_waf_2025:
payment_protection:
- card_data_tokenization: real_time
- transaction_risk_scoring: ml_powered
- fraud_pattern_detection: advanced
regulatory_compliance:
- pci_dss_4_0: automated_compliance
- sox_reporting: integrated
- real_time_monitoring: enabledPerformance Predictions
Latency Improvements
Expected Performance Gains (2025-2030):
Current Average Latency: 2-5ms
2025 Target: 0.5-1ms
2030 Prediction: 0.1-0.3ms
Throughput Improvements:
Current: 100K-1M requests/second
2025: 1M-10M requests/second
2030: 10M-100M requests/secondCost Reductions
Projected Cost Evolution:
javascriptconst costProjections = {
2025: {
cloudWAF: "40% cost reduction from 2023",
enterpriseWAF: "25% cost reduction",
management: "60% reduction (automation)"
},
2030: {
cloudWAF: "70% cost reduction from 2023",
enterpriseWAF: "50% cost reduction",
management: "85% reduction (full automation)"
}
};Frequently Asked Questions
What is a Web Application Firewall in simple terms?
A Web Application Firewall (WAF) is like a security guard for your website that checks every visitor (request) before letting them enter your web application. It blocks malicious visitors while allowing legitimate users through.
How does WAF web application firewall differ from antivirus software?
WAF protects web applications from internet-based attacks in real-time, while antivirus protects individual computers from malware. WAF operates at the network level, scanning incoming web traffic, whereas antivirus scans files and programs on a device.
What is web application firewall architecture?
WAF architecture typically includes:
Traffic Interception Layer: Captures incoming requests
Analysis Engine: Examines requests against security rules
Decision Engine: Determines whether to allow, block, or challenge
Logging System: Records all activities for monitoring
Management Interface: Configures rules and policies
Can you explain web application firewall meaning in business context?
In business terms, a WAF is a cybersecurity investment that protects your online revenue, customer data, and brand reputation. It prevents website attacks that could cause downtime, data breaches, and financial losses.
Which is the best web application firewall for small businesses?
For small businesses, the best options are:
Cloudflare Pro ($20/month) – Easy setup, good protection
Sucuri ($199/year) – WordPress-focused, affordable
ModSecurity (Free) – If you have technical expertise
How do I implement AWS web application firewall?
AWS WAF implementation steps:1. Create Web ACL
aws wafv2 create-web-acl --name "MyWebACL" --scope REGIONAL
2. Create rules
aws wafv2 create-rule-group --name "SQLInjectionRules"
3. Associate with resources
aws wafv2 associate-web-acl --web-acl-arn "arn:aws:wafv2:…" \
--resource-arn "arn:aws:elasticloadbalancing:…"
What’s the difference between Azure web application firewall options?
Azure offers three WAF options:
Application Gateway WAF: For load balancing + WAF
Front Door WAF: For global CDN + WAF
CDN WAF: For content delivery + basic protection
How much does web application firewall cost?
WAF costs vary significantly:
Free/Open Source: $0 (ModSecurity, NAXSI)
Cloud WAF: $20-500/month (Cloudflare, AWS WAF)
Enterprise WAF: $5,000-50,000/month (F5, Imperva)
Hardware WAF: $50,000-500,000 upfront
What’s the ROI of implementing a WAF?
Average WAF ROI is 2,000-20,000% annually because:
Average data breach costs $4.45 million
WAF prevents 80-95% of web application attacks
Downtime costs $5,600 per minute for large businesses
Compliance fines can reach millions
Cloudflare vs AWS WAF – which is better?
Cloudflare is better for:
Easy setup and management
Global CDN integration
Small to medium businesses
WordPress sites
AWS WAF is better for:
AWS-native applications
Custom rule requirements
API protection
Enterprise integrations
What makes F5 web application firewall special?
F5 Advanced WAF offers:
Behavioral Analytics: ML-powered threat detection
High Performance: 100 Gbps throughput capability
Advanced Features: Bot defense, DataSafe, API security
Enterprise Support: 24/7 professional services
Can WAF protect against zero-day attacks?
Modern WAFs provide partial zero-day protection through:
Behavioral analysis: Detects unusual patterns
Heuristic detection: Identifies suspicious behavior
Virtual patching: Temporary protection until patches available
Threat intelligence: Real-time attack pattern updates
Does WAF help with compliance requirements?
Yes, WAF helps with:
PCI DSS: Requirement 6.5.1 for web application security
GDPR: Data protection and breach prevention
HIPAA: PHI security requirements
SOX: Data integrity protection
ISO 27001: Information security controls
Does WAF slow down website performance?
Modern WAFs typically:
Add 1-5ms latency (cloud WAFs)
May improve performance through caching
Can reduce bandwidth via compression
Edge deployment minimizes impact
Optimization tips:
Use edge-deployed WAFs
Enable caching for static content
Tune rules for your application
Monitor performance metrics
How do I reduce WAF false positives?
To minimize false positives:
Baseline Traffic: Understand normal user behavior
Tune Rules: Adjust sensitivity levels gradually
Create Whitelists: Allow trusted IPs and user agents
Test Thoroughly: Use staging environments
Monitor Continuously: Review logs regularly
Why is my WAF blocking legitimate traffic?
Common causes and solutions:
Overly aggressive rules: Lower sensitivity
Missing whitelists: Add trusted sources
Application changes: Update WAF rules
User behavior changes: Retrain behavioral models
How do I monitor WAF effectiveness?
Key metrics to track:waf_monitoring:
security_metrics:
- blocked_attacks_per_day
- attack_types_distribution
- false_positive_rate
- response_time_impact
business_metrics:
- uptime_improvement
- compliance_status
- cost_savings
- incident_reduction
How will AI change web application firewall technology?
AI will transform WAFs through:
Predictive blocking: Stop attacks before they happen
Automated tuning: Self-optimizing rule sets
Behavioral learning: User-specific protection
Threat hunting: Proactive threat discovery
What is the future of cloud web application firewall?
Cloud WAF evolution includes:
Edge computing integration: Processing at network edge
Serverless architecture: Function-based protection
API-first design: Microservices security
Zero Trust integration: Identity-driven security
Conclusion
Web Application Firewalls have evolved from simple rule-based filters to sophisticated AI-powered security platforms. As cyber threats continue to grow in complexity and frequency, WAFs remain an essential component of any comprehensive web security strategy.
Key Takeaways
- Essential Protection: WAF is no longer optional for web applications
- Multiple Options: Choose based on your technical requirements and budget
- Implementation Matters: Proper configuration is crucial for effectiveness
- Continuous Evolution: WAF technology rapidly adapts to new threats
- Strong ROI: Security investment pays for itself through breach prevention
Next Steps
- Assess Your Needs: Evaluate current security posture
- Choose the Right Solution: Consider technical and business requirements
- Plan Implementation: Develop a phased deployment strategy
- Monitor and Optimize: Continuously improve WAF effectiveness
- Stay Updated: Keep pace with evolving security landscape
Whether you’re protecting a small WordPress site or a large enterprise application, implementing a Web Application Firewall is one of the most effective security investments you can make. The question isn’t whether you need a WAF, but which solution best fits your specific requirements.
For the latest WAF technologies and implementation guidance, consider consulting with security professionals or engaging with WAF vendors directly to ensure optimal protection for your web applications.
Leave a Comment