Nmap (Network Mapper) is a powerful tool used for network discovery and security auditing. Whether you’re new to cybersecurity or looking to deepen your skills, Nmap helps you discover open ports, identify services, and assess security vulnerabilities on a network. This guide will walk you through essential Nmap commands, from basic scans to more advanced techniques.
Whether you’re scanning a single device or an entire network, this guide will help you get started with Nmap and explore its full potential.
What is Nmap and How Does It Work?
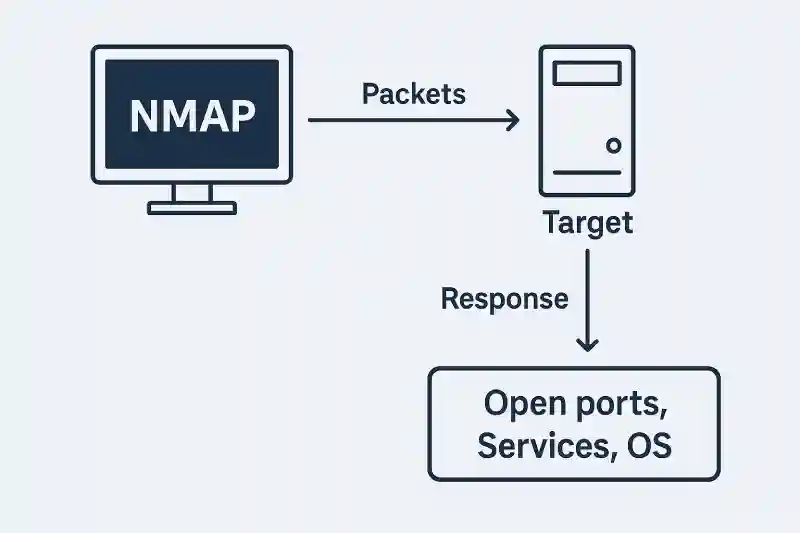
Nmap (Network Mapper) is a powerful tool used for network discovery and security auditing. It works by sending specially crafted packets to a target host and analyzing the responses. Through this, it can detect:
Possible security vulnerabilities
Which ports are open
Which services are running on those ports
What OS the target is using
Read More: Automate Everything on Windows Using WMI
Nmap Installation
Windows:
- Download from: https://nmap.org/download.html
- Run the installer and follow default setup
Linux (Debian/Ubuntu):
sudo apt update
sudo apt install nmapmacOS (with Homebrew):
brew install nmapRead More: Why and How to Disable XMLRPC.php in WordPress for Maximum Security
How to Use Nmap in Kali Linux
Kali Linux is a popular penetration testing distribution, and it comes with Nmap pre-installed.
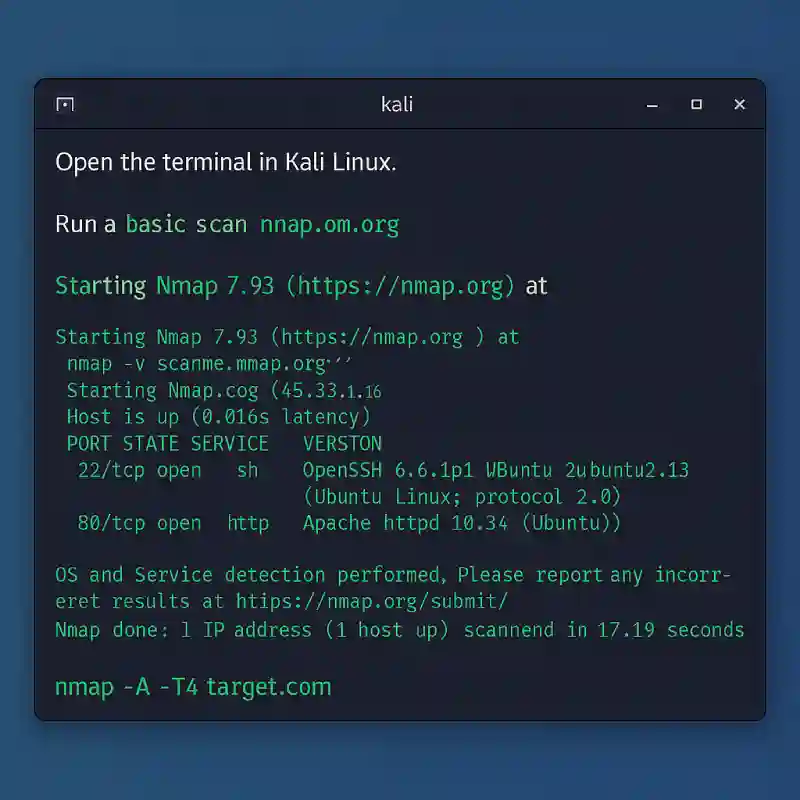
To get started:
- Open the terminal in Kali Linux.
- Run a basic scan:
nmap -v scanme.nmap.org- For a more advanced scan with OS detection, version detection, script scanning, and traceroute:
nmap -A -T4 target.comThis will give you comprehensive information about the target including services, OS, and potential vulnerabilities.
Basic Nmap Commands for Beginners
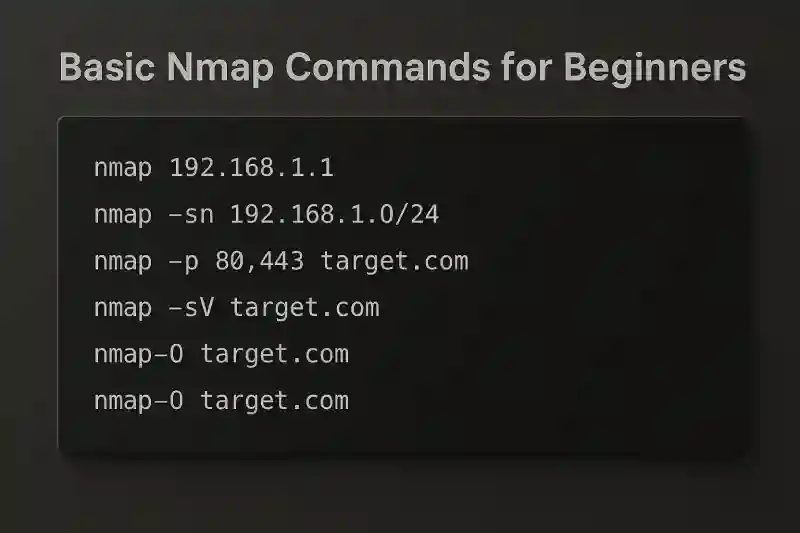
| Command | Description |
|---|---|
nmap 192.168.1.1 | Basic scan of target IP |
nmap -sn 192.168.1.0/24 | Ping scan to find live hosts |
nmap -p 80,443 target.com | Scan specific ports |
nmap -sV target.com | Detect service versions |
nmap -O target.com | Detect operating system |
Nmap Commands
Host Discovery:
nmap -sn 192.168.1.1Checks if the host is online (ping scan).
Port Scanning:
nmap 192.168.1.1Scans top 1000 common ports.
Specific Port Scan:
nmap -p 80,443 192.168.1.1Scans only port 80 and 443.
Service Detection:
nmap -sV 192.168.1.1Shows which service and version are running on open ports.
OS Detection:
nmap -O 192.168.1.1Tries to guess the target’s operating system.
How to Scan a Website Using Nmap?
To scan a website (like example.com), use:
nmap example.comTo detect services and OS:
nmap -A example.comTo find potential vulnerabilities:
nmap --script vuln example.comIntermediate Level User Topics
How to Scan Multiple IPs:
nmap 192.168.1.1 192.168.1.2 192.168.1.3or
nmap 192.168.1.1-50OS Detection:
nmap -O 192.168.1.1Find Open Ports:
nmap -p- 192.168.1.1Stealth Scan:
nmap -sS 192.168.1.1Live Host Discovery:
nmap -sn 192.168.1.0/24Nmap NSE Scripts:
nmap --script vuln target.comVulnerability Scan:
nmap -sV --script vuln target.comFirewall Evasion:
nmap -f target.comNmap + Metasploit: Export Nmap results:
nmap -oX scan.xml target.comThen import into Metasploit:
db_import scan.xmlAutomate with Cron Jobs:
crontab -eAdd:
0 2 * * * nmap -oN daily_scan.txt 192.168.1.0/24Scan for CVEs and Exploits: Use scripts or custom NSE:
nmap --script=http-vuln-cve2021-41773.nse target.comScan IP Range:
nmap 192.168.1.1-20Subnet Scan:
nmap 192.168.1.0/24Stealth Scan (SYN Scan):
nmap -sS 192.168.1.1Verbose Output:
nmap -v 192.168.1.1Output to File:
nmap -oN result.txt 192.168.1.1Advanced Nmap Usage
Nmap Scripting Engine (NSE):
nmap --script vuln 192.168.1.1Detects common vulnerabilities.
Firewall Evasion:
nmap -f 192.168.1.1Sends fragmented packets to bypass some firewalls.
Aggressive Scan:
nmap -A 192.168.1.1Performs OS detection, version detection, script scanning all in one.
Read More: Fix WMI Provider Host CPU Issues in Windows
Timing Options (Faster or slower scan):
nmap -T4 192.168.1.1Real Use Cases
- Checking which devices are connected to your home WiFi
- Detecting unauthorized devices in office network
- Checking open ports and services of a website
- Ethical hacking & penetration testing
Nmap vs Other Tools
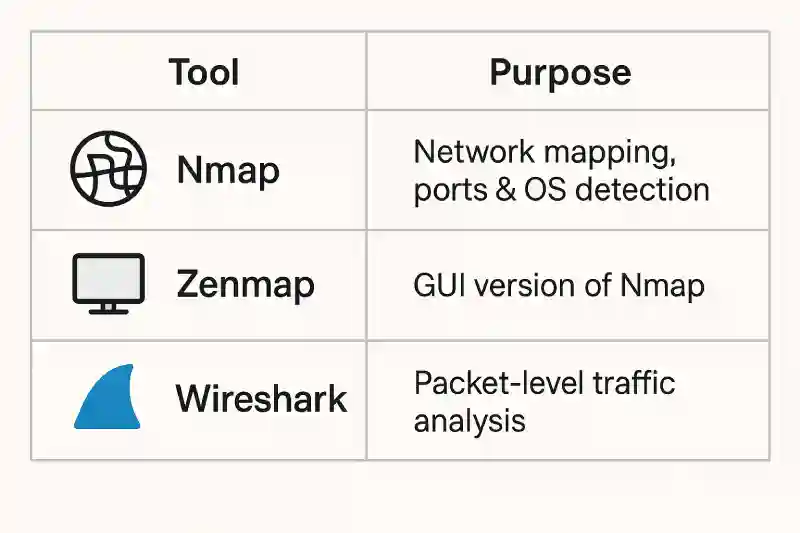
| Tool | Purpose |
|---|---|
| Nmap | Network mapping, ports & OS detection |
| Zenmap | GUI version of Nmap |
| Wireshark | Packet-level traffic analysis |
Nmap vs Wireshark – Which Is Better?
| Feature | Nmap | Wireshark |
| Purpose | Network scanning | Packet sniffing |
| GUI | No (but Zenmap exists) | Yes |
| Live Capture | No | Yes |
| Use Case | Port, OS, vuln detection | Traffic analysis |
| Skill Level | Easy to Intermediate | Intermediate to Advanced |
Use both together for deep network insights.
Nmap Cheat Sheet
| Command | Description |
|---|---|
nmap -sn | Ping Scan – Identifies live hosts in a network |
nmap -sS | SYN Scan (Stealth) – Performs a stealth scan to detect open ports |
nmap -O | OS Detection – Attempts to identify the target’s operating system |
nmap -sV | Service Version Detection – Identifies the version of services running on open ports |
nmap -A | Aggressive Scan – Detects OS, services, versions, and runs scripts |
nmap -p | Specific Port Scan – Scan specific ports (e.g., nmap -p 80,443) |
nmap -oN | Output to File – Saves scan results in a normal output format (e.g., nmap -oN result.txt) |
nmap -p- | Scan All Ports – Scans all 65,535 ports on the target |
nmap -T4 | Timing Template – Increases speed of scan (use T1 for slow scans or T5 for very fast) |
nmap -sT | TCP Connect Scan – Performs a full TCP connection to detect open ports |
nmap -sU | UDP Scan – Scans for open UDP ports on the target |
nmap -Pn | No Ping – Skips host discovery, useful when targets do not respond to ICMP requests |
nmap -v | Verbose Output – Provides detailed output during the scan |
nmap -iL | Input from File – Scans a list of IPs from a file |
nmap --script vuln | Vulnerability Scan – Uses Nmap’s NSE (Nmap Scripting Engine) to check for vulnerabilities |
nmap --script=http-vuln-cve2021-41773.nse | CVE Vulnerability Detection – Scans for specific CVE vulnerabilities (e.g., CVE-2021-41773) |
nmap -T0 | Extremely Slow Scan – For stealthy and low-profile scanning |
nmap -sN | Null Scan – Sends no flags and is useful for evading certain firewalls |
nmap --reason | Reason for Status – Displays the reason why Nmap marked the port as open or closed |
nmap -6 | IPv6 Scan – Scans IPv6 addresses and networks |
nmap -oX | Output in XML format – Saves results in XML format (e.g., nmap -oX result.xml) |
nmap --open | Show Only Open Ports – Displays only the open ports in the results |
nmap --max-retries | Set Max Retries – Limits the number of retries for a port scan |
nmap --script ftp-anon | FTP Anonymous Login – Checks for anonymous login on FTP services |
nmap --traceroute | Traceroute – Performs a traceroute to the target to identify network hops |
nmap -sI | Idle Scan – Stealth scan technique that uses an intermediary host |
nmap -sC | Default Script Scan – Runs a set of default scripts during the scan |
nmap -sF | FIN Scan – Sends a FIN packet to detect open ports, useful against firewalls |
nmap -sX | Xmas Scan – Sends a Christmas Tree packet (all flags set) to identify open ports |
nmap -sA | ACK Scan – Used to map out firewall rules and check if ports are filtered |
nmap -sW | Window Scan – Detects open ports based on TCP window size |
nmap -sM | Maimon Scan – This is a rare scan method that’s useful for bypassing certain firewalls |
nmap --scanflags | Scan flags – Customizes scan flags during the port scan |
nmap -oG | Output in Grepable format – Useful for parsing the results into other tools (e.g., nmap -oG result.gnmap) |
nmap -oA | Output in All Formats – Saves scan results in normal, XML, and grepable formats (e.g., nmap -oA result) |
nmap -p 1-65535 | Scan All TCP Ports – Scans all ports from 1 to 65535 |
nmap --source-port | Source Port – Changes the source port for the scan to avoid detection |
nmap --data-length | Send Custom Data – Allows you to send a specified number of bytes to each packet |
nmap --randomize-hosts | Randomize Host Scan Order – Randomizes the scanning order for stealth |
nmap -n | Disable DNS Resolution – Prevents Nmap from resolving hostnames to IPs |
nmap -R | Enable DNS Resolution – Forces Nmap to resolve hostnames to IPs |
nmap --exclude | Exclude Hosts – Excludes a set of IPs or ranges from the scan (e.g., nmap --exclude 192.168.1.5) |
nmap --excludefile | Exclude Hosts from a File – Excludes hosts listed in a text file |
nmap -b | FTP Bounce Scan – Bounces the scan through an FTP server |
nmap --top-ports | Scan the Top N Ports – Scans the most common ports (e.g., nmap --top-ports 100) |
nmap --append-output | Appends scan results to an existing file |
nmap --unprivileged | Scan with Low Privileges – Use when scanning on a system with low user privileges |
nmap -v -A | Verbose Aggressive Scan – Combines verbosity and aggressive scanning |
Conclusion
Nmap is a tool used by everyone from beginners to professionals. Whether you’re trying to secure your own network or learning penetration testing, Nmap is the first and strongest step.




It’s an awesome piece of writing in favor of all the online users;
they will obtain advantage from it I am sure.
Thank you so much! I’m glad you found it helpful 😊 Appreciate your kind words!
I every time spent my half an hour to read this weblog’s
posts everyday along with a cup of coffee.
Wow, that’s awesome! I’m glad you enjoy reading the posts with your coffee ☕😊 Really appreciate your daily support!
whoah this weblog is fantastic i really like studying your articles.
Stay up the great work! You recognize, a lot of individuals are searching around for this information, you can help them greatly.
Thank you so much! I’m glad you’re enjoying the articles 😄 Really appreciate your kind words and encouragement—it means a lot!
Greetings! This is my first comment here so I just wanted to
give a quick shout out and say I truly enjoy reading through your articles.
Can you suggest any other blogs/websites/forums that deal with the same topics?
Thanks for your time!
Thank you so much for your kind words! Really glad you’re enjoying the articles 😊 As for similar blogs and forums, I’ll definitely share a few recommendations soon. Appreciate you taking the time to drop your first comment here—it means a lot!
You actually make it seem so easy with your presentation but I find
this matter to be really something that I think I would never understand.
It seems too complex and very broad for me.
I’m looking forward for your next post, I will
try to get the hang of it!
When someone writes an piece of writing he/she keeps the thought of a user in his/her brain that how a user can know it. So that’s why this paragraph is outstdanding.
Wonderful blog! Do you have any hints for
aspiring writers? I’m hoping to start my own site soon but I’m
a little lost on everything. Would you recommend starting with a free platform like WordPress or go for a paid option? There are so many options out there that I’m
completely confused .. Any recommendations? Kudos!
Good site! I truly love how it is simple on my eyes and the data are well written. I am wondering how I could be notified whenever a new post has been made. I’ve subscribed to your RSS which must do the trick! Have a great day!
Thanks for ones marvelous posting! I quite enjoyed reading it, you might be a great author.I will make sure to bookmark your blog and will come back in the foreseeable future. I want to encourage one to continue your great writing, have a nice holiday weekend!
I enjoy what you guys tend to be up too. This type of clever work and reporting!
Keep up the superb works guys I’ve added you guys to our blogroll.
very good post, i actually love this website, keep on it
Hi every one, here every person is sharing these kinds of knowledge, therefore it’s good to read this blog, and I used to pay a quick visit this blog daily.
Do you have any video of that? I’d care to find out more details.
Hmm it appears like your website ate my first comment (it was super long) so I guess I’ll just sum it up what I had written and say, I’m thoroughly enjoying your blog. I as well am an aspiring blog writer but I’m still new to the whole thing. Do you have any points for novice blog writers? I’d genuinely appreciate it.
What i don’t understood is actually how you are not actually much more well-liked than you might be right now. You are very intelligent. You realize therefore significantly relating to this subject, produced me personally consider it from a lot of varied angles. Its like women and men aren’t fascinated unless it is one thing to accomplish with Lady gaga! Your own stuffs great. Always maintain it up!
It’s a pity you don’t have a donate button! I’d definitely donate to this fantastic blog! I guess for now i’ll settle for bookmarking and adding your RSS feed to my Google account. I look forward to new updates and will share this blog with my Facebook group. Talk soon!
I appreciate, lead to I found exactly what I was looking for.
You’ve ended my four day long hunt! God
Bless you man. Have a nice day. Bye
I do agree with all of the concepts you’ve introducedon your post. They’re really convincing and will definitely work.Nonetheless, the posts are very brief for newbies.May just you please extend them a bit from subsequent time?Thanks for the post.
Spot on with this write-up, I really believe this site needs much more attention. I’ll probably be returning to read through more, thanks for the info!
I don’t even know how I ended up here, but I thought this post was great. I do not know who you are but definitely you’re going to a famous blogger if you are not already 😉 Cheers!
What’s up to all, the contents existing at this site are truly amazing for people experience, well, keep up the
nice work fellows.
Greetings! Very useful advice within this post!
It’s the little changes that produce the most significant changes.
Thanks for sharing!
Great beat ! I wish to apprentice while you amend your web site, how could i subscribe for a blog site?
The account helped me a acceptable deal. I had been tiny
bit acquainted of this your broadcast provided
bright clear concept
whoah this weblog is excellent i love studying your posts.
Stay up the good work! You already know, lots of individuals are searching around for this information, you can help them greatly.
Hello There. I found your blog using msn. This is an extremely
well written article. I will make sure to bookmark it
and return to read more of your useful information. Thanks for the
post. I will certainly comeback.
I’m curious to find out what blog platform you’re working with?
I’m having some minor security issues with my latest
blog and I would like to find something more secure.
Do you have any solutions?
Interesting blog! Is your theme custom made or did you download it from somewhere? A design like yours with a few simple adjustements would really make my blog stand out. Please let me know where you got your theme. Kudos
wonderful issues altogether, you simply gained
a logo new reader. What may you suggest about your submit that you simply made a few days in the past?
Any positive?
Hello there! I simply would like to give you a big thumbs up for the excellent information you have here on this post. I am coming back to your site for more soon.
Write more, thats all I have to say. Literally, it seems as though you relied on the video to make your point. You obviously know what youre talking about, why throw away your intelligence on just posting videos to your weblog when you could be giving us something informative to read?