If you’re running a WordPress site, you might have come across XMLRPC.php—but what is it, and why is it important? Simply put, XMLRPC.php is a communication protocol that allows your WordPress website to interact with external applications and services, such as mobile apps, Jetpack, and other remote publishing tools. While this functionality can be very useful, it also comes with its own set of security risks.
In this comprehensive guide, we’ll explain what XMLRPC.php is, when it’s necessary to keep it enabled, and whether it’s safe to disable. We’ll also explore its potential security vulnerabilities, how to check if it’s active, and how to safely disable it if needed. Whether you’re a beginner, a tech-savvy blogger, or a developer, this article will help you understand the ins and outs of XMLRPC.php and guide you in making informed decisions for your WordPress website.
User Complaints & Pain Points (Real Examples from Forums)
Users on forums have mentioned complaints like:
- “I’m facing brute-force attacks via the XMLRPC file.”
- “My site’s speed has dropped due to XMLRPC requests.”
- “Jetpack or mobile app stopped working because XMLRPC is disabled.”
What is XMLRPC.php?
XMLRPC.php is a WordPress file that allows communication between your website and external systems. It works as part of the XML-RPC protocol (Extensible Markup Language – Remote Procedure Call) to enable remote access and control of your WordPress site.
This XML-RPC protocol allows other applications, such as mobile apps (like the WordPress mobile app), and third-party services (such as Jetpack, IFTTT, and Zapier) to interact with your WordPress site remotely.

Here’s how XMLRPC.php works in simple terms:
- If you’re managing your WordPress site using the WordPress mobile app, Jetpack, or other external services like IFTTT, those apps send a request to XMLRPC.php to perform actions (like creating posts, reading stats, etc.) on your WordPress site.
- XMLRPC acts as a “bridge” that receives requests from the outside world, processes them, and sends responses back to the requesting app or service.
Why is it Important?
- Remote Management: It allows remote posting, and data syncing with mobile apps or other external tools.
- Jetpack Dependency: The Jetpack plugin, used by millions of WordPress users, heavily relies on XMLRPC.php for things like stats, backups, and security services.
How Does the XML-RPC Protocol Work?
XML-RPC is a protocol that communicates remote requests to the WordPress server. It sends data in XML format and communicates via HTTP. When you interact with WordPress via mobile apps or Jetpack, the XMLRPC request gets processed by the server, and data is fetched in response.
Read More: How to Use MBR for Windows Installation, USB Boot, and Repair
Role of XMLRPC.php in WordPress
XMLRPC has different roles depending on the use case:
– For Mobile Apps
If you’re managing your WordPress site using the WordPress mobile app, XMLRPC.php is essential. The app communicates with your WordPress site through this file.
– For Jetpack Plugin
The popular Jetpack plugin also uses XMLRPC.php to function. It relies on this file for stats, backups, and other services.
– For Remote Publishing Tools (IFTTT, Feedzy, etc.)
If you’re using IFTTT or Zapier to automate tasks, XMLRPC.php is also used to push data remotely to WordPress.
How to Check if XMLRPC is Active or Not?
To check if XMLRPC is active, simply append /xmlrpc.php to your website URL and open it in a browser. If you see the message “XML-RPC server accepts POST requests only.”, it means the file is active.

When is it Necessary to Keep XMLRPC.php Enabled?
Keep it enabled if:
- You manage your site via the WordPress mobile app
- You use Jetpack or remote publishing tools
You can disable it if:
- You only use the traditional web interface
- You have security concerns and don’t need remote access
How to Safely Disable XMLRPC.php? (3 Methods)
- If you’re not using external apps or services like Jetpack or mobile apps, you might consider disabling XMLRPC to improve security and performance.
- However, if you rely on features like Jetpack, mobile apps, or IFTTT, disabling XMLRPC will disrupt those functionalities.
Read More: ESET Versions Compared: Pick the Right One + Fix Common Issues
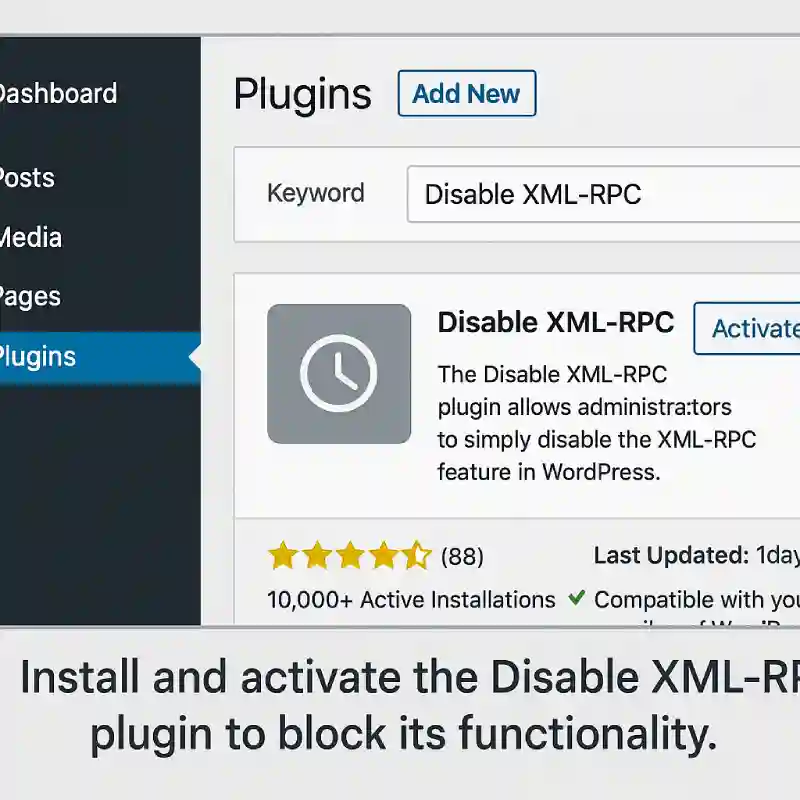
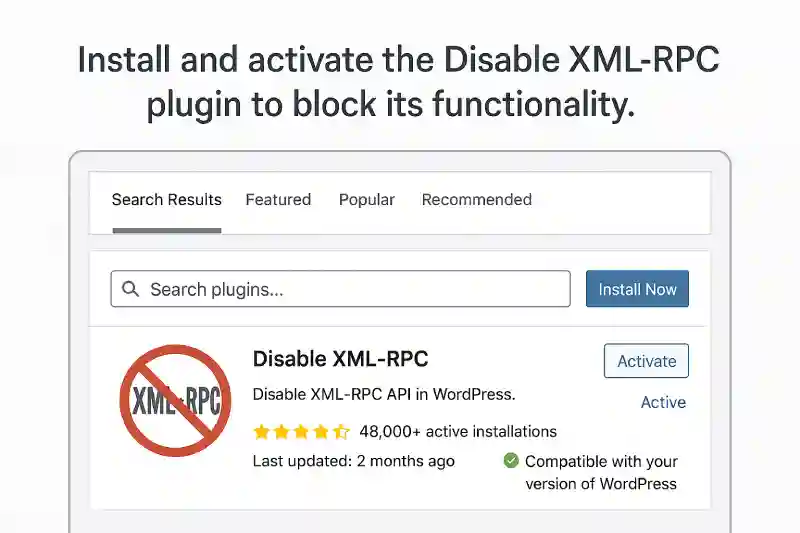
1. Using a Plugin (For Beginners)
Install the “Disable XML-RPC” plugin. Once activated, the plugin will automatically block XMLRPC.
2. Through .htaccess File (For Advanced Users)
Add the following code to your .htaccess file:
apacheCopyEdit<Files xmlrpc.php>
Order Allow,Deny
Deny from all
</Files>
3. Via Code (functions.php)
Add this snippet to your theme’s functions.php file:
phpCopyEditadd_filter('xmlrpc_enabled', '__return_false');
Will Disabling XMLRPC.php Break Jetpack/Apps?
If you’re using Jetpack or mobile apps, disabling XMLRPC will break their functionality. So, before disabling, ensure that you don’t rely on these tools.
Pros & Cons of Disabling XMLRPC.php
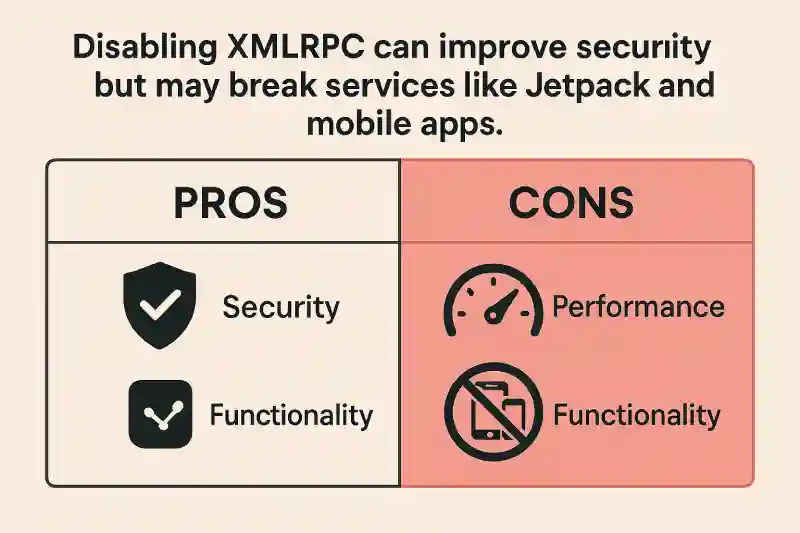
Pros:
- Improved security
- Better performance (fewer requests to the server)
Cons:
- Jetpack and mobile apps won’t work
- External tools like IFTTT won’t function
Advanced Control: How to Block Access Based on IP or Partially Disable XMLRPC?
If you want to keep XMLRPC but allow access only from certain IP addresses, you can add this to your .htaccess file:
apacheCopyEdit<Files xmlrpc.php>
Order Deny,Allow
Deny from all
Allow from 123.456.789.000
</Files>
Is XMLRPC.php Necessary in Today’s World?
XMLRPC is necessary if you use remote tools or mobile apps. If you only use WordPress’s web interface, this file is not required. But if you’re using Jetpack or mobile apps, it should remain active.
XMLRPC vs REST API: Which is Better in 2025?
REST API is a modern, more secure alternative to XMLRPC. If you’re looking for new features or security improvements, the REST API might be a better option than XMLRPC.
Read More: How to Fix “MBR2GPT Failed” Error in Windows
Common Vulnerabilities of XMLRPC.php
There are several security risks associated with XMLRPC:
– Brute Force Login Attempts
Hackers can use this file to launch multiple login attempts, facilitating brute-force attacks.
– DDoS via Pingback
Hackers misuse XMLRPC by sending pingback requests to multiple servers, causing a denial-of-service attack.
– Bandwidth/CPU Usage
Without proper security, XMLRPC can create unnecessary load on your server, affecting bandwidth and CPU usage.
What Do Security Plugins Alert You About Regarding XMLRPC?
If you’re using WordPress security plugins (like Wordfence or iThemes), you’ll often get alerts related to XMLRPC vulnerabilities, such as:
- Multiple login attempts
- Excessive pingback requests
- Unusual traffic spikes
When Can XMLRPC.php Be a Security Risk?
While XMLRPC provides useful functionalities, it can also introduce security concerns, including:
- Brute Force Attacks: Hackers can exploit XMLRPC.php to launch brute-force login attacks on your site.
- DDoS (Distributed Denial of Service): XMLRPC is vulnerable to misuse in Pingback DDoS attacks, which can overload a server with massive amounts of traffic.
- Unwanted Requests: Malicious bots may use XMLRPC to flood your server with unnecessary requests, affecting your site’s performance.
Solutions for Specific User Complaints
- Brute-force attacks: You’ve mentioned brute-force attacks, but you could elaborate on solutions like limiting login attempts using plugins (e.g., Limit Login Attempts Reloaded) or reCAPTCHA to mitigate attacks.
- Impact on Performance: If users are seeing performance issues due to XMLRPC requests, suggesting the use of caching plugins (e.g., W3 Total Cache) or server-side optimizations to handle high request volumes might be helpful.
REST API vs XMLRPC
It would be beneficial to add a detailed comparison between XMLRPC and the newer REST API (which is more secure and faster). While you briefly mention REST API, users interested in upgrading from XMLRPC might want more guidance on:
- How to switch from XMLRPC to REST API
- What changes might occur in their workflow
- Pros/cons specific to developers or users transitioning
Read More: Fix WMI Provider Host CPU Issues in Windows
User-Friendly Alternatives to Disabling XMLRPC
For users who are unsure about fully disabling XMLRPC, you can recommend:
- Limiting XMLRPC functionality (only enabling specific functions like pingbacks or remote posting)
- Using firewall settings to filter traffic coming through XMLRPC, thereby improving security without disabling it entirely.
Additional Security Considerations
Mention the importance of keeping WordPress, themes, and plugins updated to protect against security vulnerabilities, even if XMLRPC is disabled. You can also recommend tools like Sucuri for monitoring unauthorized access.
Advanced Users/Developers
Provide more advanced options for developers who may need greater control over how XMLRPC functions:
- Using custom endpoints in REST API instead of XMLRPC for remote services
- Programmatic solutions for selectively disabling XMLRPC methods or filtering incoming requests based on custom logic
Conclusion
This article provides a comprehensive breakdown of XMLRPC.php in WordPress — from explaining its function to offering actionable advice on whether to disable it or not. If you have any further questions or need clarification, feel free to leave a comment!


Very thoughtful writing, thanks!