Cross-Site Scripting (XSS) has become the most dangerous web vulnerability of 2025, affecting millions of websites worldwide. Whether you’re searching for “what is XSS” or looking for advanced XSS payloads and prevention techniques, this complete guide covers everything you need to know about XSS attacks, vulnerabilities, and protection methods.
What is XSS? Complete Definition and Overview
XSS (Cross-Site Scripting) is a web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. When these scripts execute in a victim’s browser, they can steal sensitive information, hijack user sessions, or perform actions on behalf of the user.
Why XSS Attacks are So Dangerous
XSS vulnerabilities represent one of the most critical security threats because they:
- Steal User Data: Access cookies, session tokens, and personal information
- Hijack User Sessions: Take complete control of user accounts
- Spread Malware: Infect users’ devices with malicious software
- Perform Phishing Attacks: Redirect users to fake login pages
- Damage Business Reputation: Cause loss of customer trust and revenue
How XSS Attacks Work
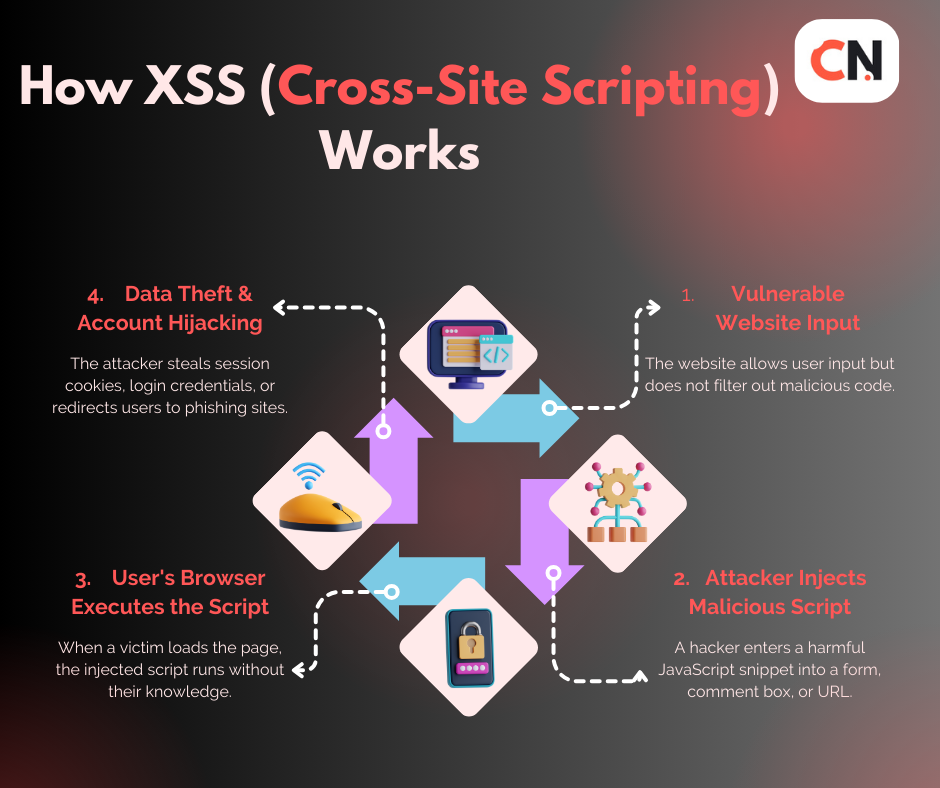
XSS attacks exploit web applications that don’t properly validate user input. When a website displays user-submitted content without proper sanitization, attackers can inject malicious JavaScript that executes in other users’ browsers.
The attack typically follows this pattern:
- Attacker finds a vulnerable input field
- Injects malicious script payload
- Script gets stored or reflected by the web application
- Victim views the compromised page
- Malicious script executes in victim’s browser
- Attacker gains access to sensitive data
Types of XSS Attacks: Complete Breakdown
Stored XSS (Persistent XSS)
Stored XSS is the most dangerous type of XSS vulnerability. The malicious script is permanently stored on the target server and executes every time a user visits the affected page.
Common Stored XSS Locations:
- User comments and reviews
- Forum posts and messages
- Profile information and bios
- File uploads and attachments
- Database entries and logs
Real-World Stored XSS Examples:
- E-commerce Sites: Malicious product reviews that steal customer payment information
- Social Media Platforms: Infected posts that spread malware to all viewers
- Support Forums: Compromised help topics that harvest user credentials
- Blog Comments: Persistent scripts that track user behavior across visits
Reflected XSS (Non-Persistent XSS)
Reflected XSS occurs when malicious scripts are immediately returned by a web application without being stored. These attacks are typically delivered through malicious URLs or form submissions.
Reflected XSS Attack Scenarios:
- Search Results: Malicious search queries that execute when results are displayed
- Error Messages: Crafted URLs that trigger script execution in error pages
- Form Submissions: Malicious data that gets reflected back to the user
- URL Parameters: Script injection through GET parameters
Reflected XSS Examples:
- Phishing emails containing malicious links
- Social engineering attacks through instant messages
- Compromised advertisements and pop-ups
- Malicious QR codes leading to XSS URLs
DOM-Based XSS
DOM XSS is a client-side vulnerability where the attack payload is executed through manipulation of the Document Object Model (DOM) in the victim’s browser. The vulnerability exists entirely in the client-side code.
DOM XSS Characteristics:
- Script execution happens entirely in the browser
- Malicious payload never reaches the server
- Attack manipulates JavaScript and DOM objects
- Often involves unsafe JavaScript functions
Common DOM XSS Vulnerabilities:
- Unsafe URL parameter processing
- Dangerous innerHTML assignments
- Insecure postMessage handlers
- Vulnerable JavaScript routing
XSS Payloads and Cheat Sheet
Basic XSS Payloads
Understanding XSS payloads is essential for both testing and defending against these attacks. Here are the most common XSS payload types:
Simple Alert Payloads:
- Basic JavaScript execution test
- Browser compatibility verification
- Initial vulnerability confirmation
- Quick penetration testing
Image-Based Payloads:
- Bypass basic script filtering
- Execute through HTML attributes
- Work in restricted environments
- Difficult to detect visually
Event Handler Payloads:
- Trigger through user interactions
- Execute without script tags
- Bypass Content Security Policy
- Work in various HTML contexts
Advanced XSS Payloads
Filter Bypass Techniques:
- Case variation methods
- Encoding and obfuscation
- HTML entity manipulation
- Unicode character substitution
Steganographic Payloads:
- Hidden in image metadata
- Concealed in CSS properties
- Embedded in URL fragments
- Disguised as legitimate content
XSS Payloads from GitHub
The cybersecurity community maintains extensive XSS payload repositories on GitHub platforms:
PayloadsAllTheThings
- Comprehensive XSS payload collection
- Regular updates with new techniques
- Community-tested and verified payloads
- Categorized by attack type and target
OWASP XSS Filter Evasion Cheat Sheet
- Official security guidelines
- Professional-grade prevention methods
- Industry-standard best practices
- Regularly updated threat intelligence
XSS Hunter Payloads
- Specialized blind XSS detection
- Real-time execution monitoring
- Detailed vulnerability reporting
- Professional penetration testing tools
Blind XSS Payloads
Blind XSS attacks execute in contexts where attackers cannot directly observe the results, making them particularly dangerous for enterprise environments.
Blind XSS Attack Vectors:
- Support ticket systems
- Admin panel interfaces
- Log file processing systems
- Email notification systems
- Internal monitoring tools
Blind XSS Detection Methods:
- Out-of-band HTTP requests
- DNS query monitoring
- Email notification triggers
- Third-party logging services
XSS Vulnerability Assessment
Common XSS Vulnerability Locations
Input Fields and Forms:
- Search boxes and query parameters
- Contact forms and feedback systems
- User registration and profile updates
- Comment sections and message boards
URL Parameters:
- GET request parameters
- Fragment identifiers and anchors
- Routing parameters in SPAs
- API endpoint parameters
HTTP Headers:
- User-Agent strings
- Referer headers
- Custom application headers
- Authentication tokens
XSS Vulnerability Testing
Manual Testing Techniques:
- Input validation bypass attempts
- Context-specific payload crafting
- Filter evasion methodology
- Business logic exploitation
Automated Vulnerability Scanning:
- Web application security scanners
- XSS-specific testing tools
- Continuous security monitoring
- Integration with CI/CD pipelines
Real-World XSS Attack Examples
British Airways XSS Breach (2021)
One of the most significant XSS attacks in recent history affected British Airways, resulting in:
- 380,000+ compromised customer records
- £20 million in regulatory fines
- Massive reputation damage
- Class-action lawsuits
The attack exploited a stored XSS vulnerability in the airline’s payment processing system, allowing attackers to harvest customer payment card details for months before detection.
Fortnite XSS Vulnerability (2018)
Epic Games’ popular Fortnite platform suffered a major XSS vulnerability that enabled:
- Account takeovers and unauthorized access
- In-game currency theft
- Personal information exposure
- Unauthorized in-app purchases
The vulnerability was discovered in the game’s web-based authentication system, highlighting the importance of securing all application components.
Social Media Platform XSS Incidents
Major social media platforms have experienced multiple XSS vulnerabilities:
- Twitter: Self-propagating XSS worms affecting millions of users
- Facebook: Stored XSS in profile information and posts
- LinkedIn: Reflected XSS in messaging and connection features
- Instagram: DOM-based XSS in image sharing functionality
XSS vs CSRF: Understanding the Differences
XSS (Cross-Site Scripting)
- Injects malicious scripts into web pages
- Executes in victim’s browser context
- Targets client-side vulnerabilities
- Steals data and hijacks sessions
CSRF (Cross-Site Request Forgery)
- Forces unwanted actions on authenticated users
- Exploits user’s existing session
- Targets server-side state changes
- Performs unauthorized operations
Key Distinction: XSS focuses on script execution and data theft, while CSRF focuses on unauthorized action execution.
XSS and CSRF Combined Attacks
Sophisticated attackers often combine XSS and CSRF techniques to:
- Bypass CSRF protection mechanisms
- Steal anti-CSRF tokens through XSS
- Perform complex multi-step attacks
- Maintain persistent access to accounts
XSS Prevention and Protection
Input Validation and Sanitization
Server-Side Validation:
- Whitelist-based input filtering
- Strict data type validation
- Length and format restrictions
- Business logic validation
Client-Side Validation:
- Real-time input checking
- User experience improvement
- Additional security layer
- Never rely on alone
Output Encoding and Escaping
Context-Aware Encoding:
- HTML context encoding
- JavaScript context encoding
- CSS context encoding
- URL context encoding
Framework-Specific Protection:
- React automatic escaping
- Angular built-in sanitization
- Vue.js template security
- Modern framework advantages
Content Security Policy (CSP)
CSP Implementation:
- Script source restrictions
- Inline script prevention
- Trusted domain whitelisting
- Nonce-based script execution
Advanced CSP Features:
- Report-only mode testing
- Violation reporting
- Dynamic policy updates
- Browser compatibility considerations
X-XSS-Protection Header
While largely deprecated in modern browsers, the X-XSS-Protection header provided basic XSS filtering:
Header Values:
- Disable XSS filtering
- Enable basic protection
- Block page rendering on detection
- Report violations to specified URI
Modern Alternative: Content Security Policy (CSP) provides superior protection and should be used instead of X-XSS-Protection.
XSS Testing Tools and Methodologies
Professional XSS Testing Tools
Burp Suite Professional
- Comprehensive web application testing
- Advanced XSS payload generation
- Automated vulnerability scanning
- Professional penetration testing
OWASP ZAP (Zed Attack Proxy)
- Open-source security testing
- Community-maintained updates
- Extensive plugin ecosystem
- Free alternative to commercial tools
XSSHunter Platform
- Specialized blind XSS detection
- Real-time payload monitoring
- Detailed execution reports
- Cloud-based testing infrastructure
Manual XSS Testing Techniques
Context-Based Testing:
- HTML context injection
- JavaScript context exploitation
- CSS context manipulation
- URL context injection
Filter Bypass Testing:
- Encoding variation attempts
- Case sensitivity testing
- Character substitution methods
- Obfuscation techniques
OWASP XSS Prevention Guidelines
OWASP XSS Prevention Cheat Sheet
The OWASP (Open Web Application Security Project) provides comprehensive XSS prevention guidelines:
Rule 1: Never Insert Untrusted Data
- Avoid direct HTML insertion
- Use parameterized queries
- Implement proper templating
- Validate all data sources
Rule 2: HTML Encode Before Insertion
- Encode special characters
- Use framework encoding functions
- Apply context-appropriate encoding
- Never trust user input
Rule 3: JavaScript Encode for Dynamic Content
- Escape JavaScript contexts
- Use JSON encoding methods
- Avoid string concatenation
- Implement safe data passing
Rule 4: CSS Encode for Style Contexts
- Sanitize CSS properties
- Validate color values
- Restrict dangerous CSS functions
- Use CSS framework protection
Rule 5: URL Encode for URL Parameters
- Encode URL components
- Validate URL schemes
- Restrict dangerous protocols
- Use proper URL construction
OWASP Security Standards
OWASP Top 10 Web Application Security Risks:
- XSS consistently ranks in top vulnerabilities
- Regular updates reflect threat landscape
- Industry-standard security benchmark
- Compliance requirement reference
Advanced XSS Protection Techniques
Web Application Firewalls (WAF)
WAF XSS Protection:
- Real-time attack detection
- Signature-based filtering
- Behavioral analysis
- Cloud-based protection services
Popular WAF Solutions:
- Cloudflare Web Application Firewall
- AWS WAF and Shield
- Azure Application Gateway
- Akamai Web Application Protector
Runtime Application Self-Protection (RASP)
RASP Benefits:
- Application-level protection
- Real-time threat detection
- Minimal false positives
- Development integration
Browser Security Features
Modern Browser Protection:
- Built-in XSS filtering
- Content Security Policy support
- Secure cookie handling
- Same-origin policy enforcement
XSS in Different Technologies
SQL Injection vs XSS
SQL Injection:
- Targets database systems
- Server-side vulnerability
- Data manipulation and theft
- Backend system compromise
XSS:
- Targets web browsers
- Client-side vulnerability
- Session hijacking and theft
- Frontend system compromise
Combined Attacks: Sophisticated attackers often chain SQL injection and XSS for maximum impact.
DOM Manipulation and XSS
DOM-Based Vulnerabilities:
- Client-side JavaScript flaws
- Browser-specific attack vectors
- Single Page Application risks
- Modern web framework challenges
XSS in API Endpoints
REST API XSS:
- JSON response injection
- Parameter pollution attacks
- Header manipulation
- Authentication bypass
GraphQL XSS:
- Query injection attacks
- Schema manipulation
- Resolver vulnerabilities
- Subscription hijacking
Clickjacking and XSS Combinations
Clickjacking Fundamentals
Clickjacking (UI redressing) tricks users into clicking on hidden elements, often combined with XSS for enhanced effectiveness:
Combined Attack Scenarios:
- XSS payload delivery through clickjacking
- Session hijacking enhancement
- Multi-vector attack strategies
- Social engineering amplification
Protection Against Combined Attacks
X-Frame-Options Header:
- Prevent iframe embedding
- Clickjacking protection
- Legacy browser support
- Simple implementation
Frame Ancestors CSP:
- Modern clickjacking prevention
- Granular control options
- Better browser support
- Enhanced security features
Emerging XSS Threats and Trends
AI-Powered XSS Attacks
Machine Learning in XSS:
- Automated payload generation
- Filter bypass optimization
- Target reconnaissance
- Attack vector identification
IoT Device XSS Vulnerabilities
Internet of Things Security:
- Embedded web interfaces
- Limited security updates
- Default credential exploitation
- Network lateral movement
Progressive Web App (PWA) XSS
PWA-Specific Vulnerabilities:
- Service worker manipulation
- Web app manifest injection
- Push notification abuse
- Offline functionality exploitation
XSS Security Testing Checklist
Pre-Deployment Testing
Development Phase:
- Input validation implementation
- Output encoding verification
- CSP policy configuration
- Framework security features
Testing Phase:
- Automated vulnerability scanning
- Manual penetration testing
- Code review processes
- Security regression testing
Post-Deployment Monitoring
Continuous Monitoring:
- Real-time attack detection
- Security log analysis
- Vulnerability assessment updates
- Incident response procedures
Regular Security Audits:
- Third-party security assessments
- Compliance verification
- Threat landscape updates
- Security training programs
Industry-Specific XSS Considerations
Financial Services XSS Protection
Banking and Finance:
- PCI DSS compliance requirements
- Customer data protection
- Regulatory reporting obligations
- High-value target considerations
Healthcare XSS Security
HIPAA Compliance:
- Patient data protection
- Medical record security
- Healthcare provider obligations
- Privacy regulation compliance
E-commerce XSS Prevention
Online Retail Security:
- Customer payment protection
- Shopping cart security
- User account safety
- Business reputation management
XSS Resource Libraries and Tools
GitHub XSS Resources
Popular XSS Repositories:
- PayloadsAllTheThings comprehensive collection
- XSS-Payload-List community contributions
- Awesome-XSS curated resources
- XSS-Cheat-Sheet quick reference guides
Security Research Platforms
Bug Bounty Platforms:
- HackerOne XSS disclosures
- Bugcrowd vulnerability reports
- Synack security research
- Open Bug Bounty community
Educational Resources
XSS Learning Platforms:
- OWASP WebGoat practice environment
- PortSwigger Web Security Academy
- VulnHub XSS challenges
- HackTheBox web exploitation
XSS Prevention Best Practices Summary
Development Best Practices
Secure Coding Guidelines:
- Never trust user input
- Implement proper input validation
- Use framework security features
- Apply defense-in-depth strategies
Security-First Development:
- Security requirements integration
- Threat modeling processes
- Secure development lifecycle
- Regular security training
Organizational Security Measures
Security Governance:
- Security policy development
- Incident response procedures
- Regular security assessments
- Compliance monitoring
Team Training and Awareness:
- Developer security education
- Regular security updates
- Threat intelligence sharing
- Security culture promotion
Conclusion
Cross-Site Scripting remains one of the most persistent and dangerous web security vulnerabilities in 2025. Understanding XSS attacks, from basic concepts to advanced exploitation techniques, is crucial for anyone involved in web development, security testing, or digital business operations.
FAQs
How dangerous is an XSS attack?
XSS attacks can be extremely dangerous, leading to data theft, session hijacking, phishing, and malware infections. Attackers can steal login credentials, compromise user accounts, and even gain control of entire web applications.
What are some real-world XSS attack examples?
Some notable XSS attack incidents include the British Airways data breach, Fortnite account theft, and vulnerabilities found in Facebook and Twitter. These incidents resulted in financial loss and reputational damage.
How can I check if my website is vulnerable to XSS?
You can use Burp Suite, OWASP ZAP, and other security tools to test for XSS vulnerabilities. Conducting regular penetration testing and code audits is also essential.
What is the difference between XSS and CSRF?
While XSS allows attackers to inject malicious scripts into web pages, CSRF (Cross-Site Request Forgery) tricks users into performing unintended actions without their consent, such as changing passwords or making unauthorized transactions.
Can XSS be prevented completely?
Yes, by following security best practices like input validation, CSP implementation, secure cookie settings, and using secure frameworks, you can significantly reduce the risk of XSS attacks.








Leave a Comment