XML External Entity (XXE) attacks are a serious cybersecurity threat that can compromise sensitive data, expose system files, and even lead to remote code execution (XXE to RCE). Attackers exploit XXE vulnerabilities in improperly configured XML parsers, injecting XXE payloads to access restricted information.
XML External Entity (XXE) vulnerabilities present significant security challenges for applications that process XML. When exploited, these vulnerabilities allow attackers to manipulate XML processing and access sensitive data, or even execute harmful code. This listicle outlines critical aspects of XXE vulnerabilities, offers real-world insights, and suggests practical strategies for mitigation.
Understanding XXE
XXE stands for XML External Entity, a type of attack that affects XML parsers. This vulnerability takes advantage of the way XML handles external entities. As applications increasingly depend on XML for data interchange, understanding XXE vulnerabilities becomes essential for maintaining cybersecurity. These attacks have existed since the advent of XML, but they remain a pressing issue due to the broad use of XML in web applications today.
This can lead to:
- Data exfiltration (reading sensitive files)
- Denial-of-service (DoS) attacks
- Server-Side Request Forgery (SSRF)
- XXE to RCE, where attackers gain control over a system
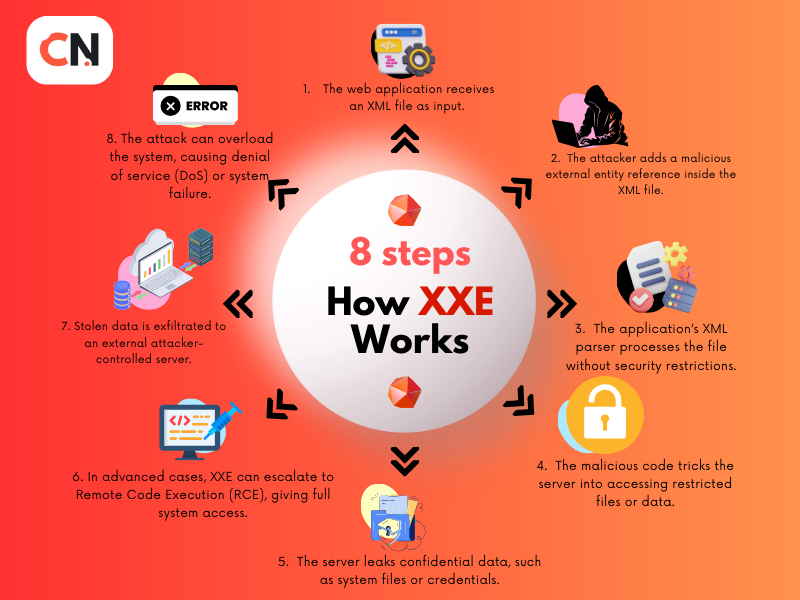
How XXE Works
XML is a markup language used to encode documents in a format that is both human-readable and machine-readable. Its use of external entities makes it flexible but can also lead to vulnerabilities. When an XML parser processes an XML document, an attacker can inject harmful entities that the parser interprets. For example, by manipulating the XML structure, attackers might redirect requests to sensitive files on a server, potentially leading to severe data breaches.
Read More: What is N8N Ai Agent and How it Works
An XXE attack takes advantage of applications that parse XML inputs without disabling external entity processing. By injecting XXE payloads, attackers can retrieve confidential data, interact with the internal network, or cause system failures.
XXE Attack Example
A common XXE example involves an attacker injecting a malicious XXE payload into an XML file:
<?xml version="1.0"?>
<!DOCTYPE data [
<!ENTITY xxe SYSTEM "file:///etc/passwd">]>
<data>&xxe;</data>If the application is vulnerable, it will return the contents of /etc/passwd, exposing critical system information.
Common Causes of XXE Vulnerabilities
Various factors can contribute to the presence of XXE vulnerabilities in applications. A primary cause is the absence of adequate input validation, allowing untrusted data to be processed. Insecure XML parsers that do not correctly handle external entities can also lead to exploitation. Other issues include misconfigurations in web servers and placing too much trust in user input, thereby creating avenues for attackers to inject malicious code.
1. File Disclosure Payload
Used to extract files from the server:
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>2. SSRF Payload
Forces the server to make requests to internal resources:
<!DOCTYPE foo [ <!ENTITY xxe SYSTEM "http://169.254.169.254/latest/meta-data/"> ]>3. Denial-of-Service (DoS) Payload
Creates recursive entities to overload memory:
<!DOCTYPE foo [ <!ENTITY a "&a;&a;&a;&a;&a;"> ]>XXE to RCE: How Attackers Escalate
A major risk in XXE cybersecurity is when an XXE vulnerability leads to remote code execution (XXE to RCE). Attackers can achieve this through:
- Out-of-band (OOB) XXE – Sending malicious XML that interacts with external servers.
- Java deserialization attacks – Leveraging Java libraries that deserialize XML data unsafely.
XXE Detection: How to Identify Vulnerabilities
Organizations must deploy effective XXE detection strategies, including:
- Static Code Analysis – Tools like SonarQube identify unsafe XML parsing.
- Penetration Testing – Security teams simulate XXE attacks using tools like Burp Suite.
- Automated Scanners – OWASP ZAP and Veracode help detect XXE injection vulnerabilities.
XXE Prevention: Best Practices
To prevent XXE attacks, developers must:
- Disable External Entity Processing – Ensure XML parsers do not process external entities.
- Use Safer Data Formats – Prefer JSON over XML when possible.
- Employ Secure XML Libraries – Use libraries like
defusedxml(Python) orlibxml2(C/C++). - Conduct Regular Security Audits – Perform periodic XXE detection scans.
Latest XXE Cybersecurity Updates (2025)
In 2025, XXE vulnerabilities continue to be a major concern. Recent attacks have targeted:
- Cloud applications with insecure XML parsing.
- API integrations that fail to sanitize XML inputs.
- Open-source libraries with outdated XML parsers.
Organizations must remain vigilant and apply XXE prevention measures to mitigate these risks.
Real-World Examples of XXE Attacks
Several notable real-world XXE attacks highlight the risks involved. For instance, a vulnerability in the Ambari/Oozie project allowed for malicious XML entity injection, exposing sensitive information. Another case involved a web service where attackers exploited the XXE vulnerability to extract crucial data. Open-source projects have also been affected, underscoring the need for vigilance in any application that processes XML.
Identifying XXE Vulnerabilities
To find potential XXE vulnerabilities, developers should look for specific signs. Unusual application behavior after processing XML input might indicate an exploit. Tools like Burp Suite and OWASP ZAP can help identify vulnerabilities. For manual testing, attacking versions of XML documents that contain crafted external entities can highlight weaknesses.
Mitigation Strategies
Mitigating XXE vulnerabilities requires a multi-faceted approach. One effective strategy is input sanitization, ensuring that malicious content cannot be introduced through XML. Disabling external entity processing in XML parsers is another critical step. Using safer XML libraries that have built-in protections can further guard against exploitation. Implementing robust error handling and creating a security policy specifically for XML processing are also essential.
Secure Coding Practices
Adopting secure coding practices can significantly reduce the risk of XXE vulnerabilities. Developers should be cautious when handling XML input and avoid allowing external entities unless absolutely necessary. Regular code audits and reviews can identify weaknesses before they can be exploited. Additionally, education on secure XML handling among development teams is vital.
Case Studies
A detailed case study of a successful XXE exploit reveals how attackers manipulate vulnerabilities for personal gain. Understanding the attacker’s methods and the subsequent responses from the affected organization can provide valuable lessons for instituting better security measures. On the other hand, examining a company that successfully mitigated XXE vulnerabilities showcases the importance of robust security protocols.
XXE in Various Programming Languages
Different programming languages handle XML processing in unique ways, which can expose them to XXE vulnerabilities. For example, Java utilizes libraries like Xerces, while PHP utilizes various XML handling libraries. Each language has its own set of security configurations needed to mitigate XXE risks. Understanding these differences is key to developing secure applications.
Read More: XSS: A Silent Threat to Web Security & How to Prevent It
Tools for Addressing XXE
A variety of tools can assist developers in managing and identifying XXE vulnerabilities. Static analysis tools can offer insights into code vulnerabilities during the development phase. Dynamic analysis tools help ensure a preventive approach by simulating attacks in a controlled environment. Recommended tools available for developers should facilitate thorough testing and vulnerability validation.
Monitoring and Response
Monitoring and responding to potential XXE attacks is crucial for maintaining application security. Regular logging of XML interactions can help identify unusual activities. Creating a robust incident response plan designed specifically for XXE vulnerabilities ensures quick action can be taken if an exploit is detected.
Community and Resources
The cybersecurity community offers numerous resources for those interested in improving their understanding of XXE vulnerabilities. Online forums and websites dedicated to web security are excellent places to share knowledge and stay updated on the latest threats. Blogs that focus on cybersecurity, along with essential books on the topic, can also provide valuable insights.
Regulatory Compliance
Compliance with regulations like GDPR and HIPAA can impact how XML processing is handled in applications. Understanding these regulations, along with maintaining reliable audits of XML handling processes, helps organizations stay compliant while securing sensitive data against XXE vulnerabilities.
Future of XXE Vulnerabilities
As XML usage continues to rise, vigilance against XXE vulnerabilities will remain critical. Emerging technologies may introduce new complexities in XML data handling, increasing exposure to potential exploits. Ongoing education and adaptation to secure coding practices will be paramount to keep applications safe from XXE attacks.
Conclusion
XXE vulnerabilities pose a serious risk to applications that rely on XML processing. By understanding how these vulnerabilities work, identifying potential weaknesses, and implementing effective mitigation strategies, organizations can significantly reduce their exposure. Regular monitoring and community engagement will further strengthen security efforts.
FAQs
What is XXE Attack?
An XXE attack exploits XML parsers that allow external entity processing, leading to data leaks, DoS, or even RCE.
How can I detect an XXE vulnerability?
You can detect XXE vulnerabilities using security tools like OWASP ZAP, Burp Suite, or manual penetration testing.
What is an example of an XXE payload?
A simple XXE payload reads system files:
<!DOCTYPE data [ <!ENTITY xxe SYSTEM “file:///etc/passwd”> ]>
<data>&xxe;</data>
How do I prevent an XXE attack?
Follow XXE prevention best practices: disable external entity processing, use secure XML parsers, and validate inputs properly.
What is the risk of an XXE vulnerability?
An XXE vulnerability can lead to data exposure, server-side request forgery (SSRF), and remote code execution (XXE to RCE).
Is XXE still a security risk in 2025?
Yes, XXE attacks remain a top concern, especially in cloud services and API-based applications.


Leave a Comment